Blockchain technology is transcending cryptocurrency to become the backbone of space exploration, solving the industry's most complex challenges with decentralization, immutability, and transparency. From satellite security to Mars colonies, here's how blockchain is transforming our cosmic future!
💰 Core Applications:
-
Satellite communication security: Tamper-proof data transmission, eliminating single points of failure
Space supply chain management: Full traceability from manufacturing to launch
Decentralized satellite networks: Multi-party shared satellite infrastructure
Space traffic management: Real-time orbital object tracking and collision avoidance
🎯 Technical Advantages:
-
Data integrity protection: Cryptographic signatures and timestamps ensure information authenticity
Smart contract automation: Automatic payment triggers after data transmission
Transparency and traceability: Complete component records from source to integration
Decentralized architecture: Eliminates central authority, enhances network resilience
🏆 Key Innovation Projects:
-
SpaceChain: Pioneering Decentralized Satellite Infrastructure (DSI)
LEO satellite authentication: Blockchain-based identity verification protocols
NASA blockchain exploration: Secure communications and equipment procurement tracking
Space debris registry: Tamper-proof database of orbital objects
💡 Real-World Use Cases:
-
International cooperation missions: Secure data sharing between multiple agencies
Satellite constellation management: Decentralized network node verification
Spacecraft component certification: Preventing counterfeit parts usage
Space data trading: Automated data exchange and payment systems
🌌 Future Development:
-
Lunar base logistics: Complex long-distance supply chain management
Mars colony construction: Decentralized resource allocation systems
Space economy ecosystem: Transparent fair resource bidding marketplace
Interplanetary communication networks: Secure cross-planetary data transmission
⚠️ Technical Challenges:
-
Space environment adaptation: Radiation-resistant, extreme temperature hardware required
Energy consumption limits: Some consensus mechanisms have high power requirements
Network latency issues: Long-distance communication time delays
Standardization needs: Unified international space blockchain protocols
🎮 Commercial Prospects:
-
Space service democratization: Breaking traditional monopolies, encouraging innovation
Shared satellite resources: Smart contract-driven service bidding
Data integrity services: Security guarantees for space missions
Cross-border collaboration platforms: Streamlined international space cooperation
Core Revolution: Blockchain is transforming space exploration from centralized, closed systems to decentralized, open collaborative networks, paving the way for a more resilient and interconnected space economy that propels humanity's cosmic exploration into a new era.
Read the complete technical analysis and application cases: 👇 https://blog.jucoin.com/blockchain-in-space-how-its-used-in-2025/?utm_source=blog
#BlockchainInSpace #Infrastructure



JU Blog
2025-08-12 08:33
🚀 Blockchain in Space: How 2025's Cosmic Revolution is Reshaping the Universe!
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
The crypto bear market may not be here yet, but you’d better start preparing. From cold wallets to burning worthless NFTs for warmth — survival starts early. Find shelter at JuCoin while there’s still time.
Check out our YouTube Channel 👉 #CryptoBearMarket#CryptoSkits #CryptoMeme #CryptoHumor #JuCoinShorts


JuCoin Media
2025-08-06 11:16
🐻 Crypto Bear Market - Not Here Yet… But Are You Ready?
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Can I Chart Markets on the TradingView Mobile App?
TradingView has established itself as a leading platform for traders and investors seeking advanced charting and analysis tools. With its user-friendly interface and comprehensive features, it caters to both beginners and seasoned professionals. One of the key questions many users have is whether they can effectively chart markets using the TradingView mobile app. The answer is yes—TradingView’s mobile version offers robust charting capabilities that enable users to analyze financial markets on-the-go.
What Is TradingView and Why Is It Popular?
TradingView is a versatile financial platform that provides real-time market data, customizable charts, technical analysis tools, social trading features, and more. Its appeal lies in its accessibility across devices—desktop or mobile—and its extensive library of indicators and drawing tools. Whether you’re tracking stocks, forex pairs, cryptocurrencies, or commodities, TradingView offers a unified environment for market analysis.
The platform’s community aspect also enhances its value; traders share insights through public charts and discussions which foster collaborative learning. This combination of professional-grade tools with social features makes it suitable for both individual investors looking to learn more about markets and professional traders executing complex strategies.
How Does Charting Work on the TradingView Mobile App?
The mobile app version of TradingView brings much of the desktop experience directly to your smartphone or tablet. Users can access real-time data feeds from multiple exchanges worldwide—crucial for making timely trading decisions in volatile markets like cryptocurrencies or forex.
Customizing charts is straightforward on mobile devices thanks to touch-friendly interfaces. You can add various technical indicators such as moving averages (MA), Relative Strength Index (RSI), Bollinger Bands, Fibonacci retracements, among others—all essential tools for technical analysis. Drawing tools like trend lines or support/resistance levels are also available to help identify key market patterns visually.
Furthermore, users can set alerts based on specific price levels or indicator signals directly within the app. These notifications ensure you stay informed without constantly monitoring your screen—a vital feature when managing multiple positions across different assets.
Recent Updates Enhancing Mobile Charting Capabilities
In recent months, TradingView has rolled out several updates aimed at improving user experience specifically on mobile devices:
- Enhanced Touch Navigation: The interface now supports smoother gestures for zooming in/out of charts or switching between timeframes.
- Advanced Drawing Tools: New options allow more precise annotations suited for small screens.
- Performance Improvements: Faster loading times mean less lag during live market hours.
- Integration Features: Users can now connect their brokerage accounts via supported integrations allowing direct trade execution from within the app—a significant step toward seamless trading workflows.
These updates demonstrate TradingView’s commitment to providing a comprehensive yet accessible toolset tailored for mobile users who need quick insights while away from their desktops.
Can You Trade Directly From the Mobile App?
One notable development is how closely integrated TradingView has become with brokerage platforms through partnerships with popular brokers globally. This integration allows traders not only to analyze but also execute trades directly from within the app interface—streamlining decision-making processes especially during fast-moving markets like cryptocurrencies or forex.
However, this feature's availability depends on your region and broker compatibility; always verify if your preferred broker supports direct trading via TradingView before relying solely on this functionality.
Security Measures Supporting Safe Market Analysis
Security remains paramount when dealing with financial apps involving sensitive data such as account credentials or personal information. TradingView employs industry-standard encryption protocols along with two-factor authentication (2FA) options that add an extra layer of security during login attempts or trade executions through integrated brokers.
While no system guarantees absolute safety against breaches—which are rare but possible—the platform’s ongoing security enhancements aim at protecting user data while maintaining ease-of-use necessary for effective charting activities remotely.
Limitations & Considerations When Using Mobile Charts
Despite its strengths, there are some limitations worth noting:
- Screen Size Constraints: Smaller screens may limit detailed analysis compared to desktop setups; however, modern smartphones mitigate this issue significantly.
- Complex Strategies May Be Challenging: Advanced multi-indicator setups might be cumbersome due to limited space.
- Connectivity Dependency: Reliable internet connection is essential; poor network conditions could disrupt live data feeds or alert notifications.
For most retail traders engaged in routine analysis rather than ultra-complex strategies requiring multiple monitors — these limitations are manageable given current device capabilities.
Key Features Summary:
- Real-time global market data
- Customizable interactive charts
- Extensive technical indicators
- Touch-friendly drawing tools
- Alerts & notification system
- Social sharing & community engagement
- Brokerage integration options
Who Should Use Charting Features On Their Smartphone?
Mobile charting suits active traders who need quick access outside traditional office environments—such as during commutes or while traveling—or those who prefer managing their portfolios via smartphones rather than desktops exclusively. It also benefits beginner investors gaining familiarity with technical analysis without investing heavily in hardware initially.
Best Practices:
- Use high-quality internet connections during critical trades.
- Customize alerts based on key price points relevant to your strategy.
- Regularly update the app ensuring access to new features & security patches.4.Simplify your workspace by focusing only on essential indicators when analyzing markets quickly.
Final Thoughts: Is Mobile Charting Effective?
Yes—it absolutely is possible—and increasingly practical—to chart markets effectively using the TradingView mobile app today! With continuous improvements driven by user feedback and technological advancements—including enhanced touch navigation and broker integrations—the platform empowers both casual investors seeking convenience and professional traders requiring reliable analytical tools outside traditional setups.
By leveraging these capabilities responsibly—with attention paid toward security measures—you gain flexible access into global financial markets anytime anywhere—even if you're away from your desktop computer.
Keywords: tradingview mobile charting | real-time market data | technical analysis apps | cryptocurrency trading apps | best stock chart apps | portable trading solutions


Lo
2025-05-26 23:00
Can I chart markets on the TradingView mobile app?
Can I Chart Markets on the TradingView Mobile App?
TradingView has established itself as a leading platform for traders and investors seeking advanced charting and analysis tools. With its user-friendly interface and comprehensive features, it caters to both beginners and seasoned professionals. One of the key questions many users have is whether they can effectively chart markets using the TradingView mobile app. The answer is yes—TradingView’s mobile version offers robust charting capabilities that enable users to analyze financial markets on-the-go.
What Is TradingView and Why Is It Popular?
TradingView is a versatile financial platform that provides real-time market data, customizable charts, technical analysis tools, social trading features, and more. Its appeal lies in its accessibility across devices—desktop or mobile—and its extensive library of indicators and drawing tools. Whether you’re tracking stocks, forex pairs, cryptocurrencies, or commodities, TradingView offers a unified environment for market analysis.
The platform’s community aspect also enhances its value; traders share insights through public charts and discussions which foster collaborative learning. This combination of professional-grade tools with social features makes it suitable for both individual investors looking to learn more about markets and professional traders executing complex strategies.
How Does Charting Work on the TradingView Mobile App?
The mobile app version of TradingView brings much of the desktop experience directly to your smartphone or tablet. Users can access real-time data feeds from multiple exchanges worldwide—crucial for making timely trading decisions in volatile markets like cryptocurrencies or forex.
Customizing charts is straightforward on mobile devices thanks to touch-friendly interfaces. You can add various technical indicators such as moving averages (MA), Relative Strength Index (RSI), Bollinger Bands, Fibonacci retracements, among others—all essential tools for technical analysis. Drawing tools like trend lines or support/resistance levels are also available to help identify key market patterns visually.
Furthermore, users can set alerts based on specific price levels or indicator signals directly within the app. These notifications ensure you stay informed without constantly monitoring your screen—a vital feature when managing multiple positions across different assets.
Recent Updates Enhancing Mobile Charting Capabilities
In recent months, TradingView has rolled out several updates aimed at improving user experience specifically on mobile devices:
- Enhanced Touch Navigation: The interface now supports smoother gestures for zooming in/out of charts or switching between timeframes.
- Advanced Drawing Tools: New options allow more precise annotations suited for small screens.
- Performance Improvements: Faster loading times mean less lag during live market hours.
- Integration Features: Users can now connect their brokerage accounts via supported integrations allowing direct trade execution from within the app—a significant step toward seamless trading workflows.
These updates demonstrate TradingView’s commitment to providing a comprehensive yet accessible toolset tailored for mobile users who need quick insights while away from their desktops.
Can You Trade Directly From the Mobile App?
One notable development is how closely integrated TradingView has become with brokerage platforms through partnerships with popular brokers globally. This integration allows traders not only to analyze but also execute trades directly from within the app interface—streamlining decision-making processes especially during fast-moving markets like cryptocurrencies or forex.
However, this feature's availability depends on your region and broker compatibility; always verify if your preferred broker supports direct trading via TradingView before relying solely on this functionality.
Security Measures Supporting Safe Market Analysis
Security remains paramount when dealing with financial apps involving sensitive data such as account credentials or personal information. TradingView employs industry-standard encryption protocols along with two-factor authentication (2FA) options that add an extra layer of security during login attempts or trade executions through integrated brokers.
While no system guarantees absolute safety against breaches—which are rare but possible—the platform’s ongoing security enhancements aim at protecting user data while maintaining ease-of-use necessary for effective charting activities remotely.
Limitations & Considerations When Using Mobile Charts
Despite its strengths, there are some limitations worth noting:
- Screen Size Constraints: Smaller screens may limit detailed analysis compared to desktop setups; however, modern smartphones mitigate this issue significantly.
- Complex Strategies May Be Challenging: Advanced multi-indicator setups might be cumbersome due to limited space.
- Connectivity Dependency: Reliable internet connection is essential; poor network conditions could disrupt live data feeds or alert notifications.
For most retail traders engaged in routine analysis rather than ultra-complex strategies requiring multiple monitors — these limitations are manageable given current device capabilities.
Key Features Summary:
- Real-time global market data
- Customizable interactive charts
- Extensive technical indicators
- Touch-friendly drawing tools
- Alerts & notification system
- Social sharing & community engagement
- Brokerage integration options
Who Should Use Charting Features On Their Smartphone?
Mobile charting suits active traders who need quick access outside traditional office environments—such as during commutes or while traveling—or those who prefer managing their portfolios via smartphones rather than desktops exclusively. It also benefits beginner investors gaining familiarity with technical analysis without investing heavily in hardware initially.
Best Practices:
- Use high-quality internet connections during critical trades.
- Customize alerts based on key price points relevant to your strategy.
- Regularly update the app ensuring access to new features & security patches.4.Simplify your workspace by focusing only on essential indicators when analyzing markets quickly.
Final Thoughts: Is Mobile Charting Effective?
Yes—it absolutely is possible—and increasingly practical—to chart markets effectively using the TradingView mobile app today! With continuous improvements driven by user feedback and technological advancements—including enhanced touch navigation and broker integrations—the platform empowers both casual investors seeking convenience and professional traders requiring reliable analytical tools outside traditional setups.
By leveraging these capabilities responsibly—with attention paid toward security measures—you gain flexible access into global financial markets anytime anywhere—even if you're away from your desktop computer.
Keywords: tradingview mobile charting | real-time market data | technical analysis apps | cryptocurrency trading apps | best stock chart apps | portable trading solutions
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
What Blockchain Technology Uses: An In-Depth Overview
Understanding the core technology behind blockchain is essential for grasping its potential and limitations. At its heart, blockchain employs a combination of cryptography, decentralized networks, and consensus mechanisms to create a secure and transparent digital ledger system. This foundation allows blockchain to serve as a trustworthy platform for various applications across industries.
Cryptography: Securing Transactions
Cryptography is fundamental to blockchain's security features. It involves encrypting transaction data so that only authorized parties can access or modify it. Public-key cryptography, in particular, plays a vital role by generating unique key pairs—public keys used as addresses and private keys for signing transactions. This ensures that each transaction is authentic and tamper-proof. Additionally, cryptographic hashing functions produce fixed-length strings (hashes) from data inputs; these hashes are used to link blocks securely in the chain, making alterations detectable.
Decentralized Network Architecture
Unlike traditional centralized databases managed by single entities, blockchain operates on a decentralized network of computers called nodes. Each node maintains an identical copy of the entire ledger, which promotes transparency and resilience against failures or attacks. When new transactions occur, they are broadcasted across the network where nodes validate them through consensus mechanisms before adding them to the ledger.
Consensus Mechanisms: Validating Data Integrity
Consensus algorithms ensure all participants agree on the state of the ledger without relying on central authority. The two most common methods are Proof of Work (PoW) and Proof of Stake (PoS).
- Proof of Work requires miners to solve complex mathematical puzzles—a process that consumes significant computational power—to validate transactions and add new blocks.
- Proof of Stake, on the other hand, selects validators based on their holdings or stake in the network’s cryptocurrency value rather than computational effort.
These mechanisms prevent malicious activities like double-spending or fraudulent entries by making it costly or impractical for bad actors to manipulate data.
How Blockchain Uses These Technologies in Practice
The integration of cryptography, decentralization, and consensus protocols enables blockchain's wide-ranging applications:
- In finance—facilitating secure cross-border payments with reduced costs.
- In government—tracking expenditures transparently while safeguarding sensitive information.
- In entertainment—enabling NFT ownership verification within gaming ecosystems.
- In cybersecurity—protecting critical infrastructure from cyber threats through tamper-resistant ledgers.
Each application leverages these underlying technologies differently but relies fundamentally on their combined strengths for security and trustworthiness.
Recent Innovations Related to Blockchain Protocols
Advancements continue shaping how blockchain systems operate:
- Enhanced Security Measures: Newer protocols aim at reducing vulnerabilities exposed during incidents like ransomware attacks involving educational institutions such as PowerSchool’s 2025 breach.
- Legal Developments Around NFTs: Ongoing legal battles over intellectual property rights associated with popular collections like Bored Ape Yacht Club highlight evolving regulatory landscapes affecting how blockchains handle ownership verification.
- Energy-Efficient Consensus Models: To address environmental concerns linked with PoW systems’ high energy consumption—which has garnered criticism—the industry is exploring alternatives such as Proof of Stake or hybrid models that balance security with sustainability.
These innovations demonstrate both technological progressions aimed at improving robustness while navigating emerging legal frameworks.
Addressing Challenges Through Technological Choices
Despite its strengths, blockchain faces challenges rooted in its technological design:
Regulatory uncertainty complicates widespread adoption; different jurisdictions have varying rules regarding cryptocurrencies and digital assets.
Security risks persist if implementations lack proper safeguards; incidents like ransomware breaches underscore this vulnerability despite inherent cryptographic protections.
Environmental impact remains contentious due to energy-intensive processes required by some consensus algorithms; ongoing research seeks greener solutions without compromising security standards.
By understanding these technical underpinnings—including cryptographic techniques like hashing functions & public-private key pairs—and how they interact within decentralized networks governed by specific consensus protocols—stakeholders can better evaluate both opportunities and risks associated with deploying blockchain solutions effectively.
Why It Matters for Users & Businesses
For users seeking transparency or businesses aiming for secure recordkeeping—and especially those involved in finance or digital asset management—the choice of underlying technology influences trustworthiness significantly. Knowing whether a platform uses energy-efficient proof schemes versus traditional proof-of-work helps assess sustainability alongside performance metrics such as transaction speed or scalability potential.
In summary,
Blockchain technology relies heavily on advanced cryptographic methods combined with decentralized architectures supported by various consensus mechanisms like PoW or PoS. These components work together not only to secure data but also enable innovative applications across sectors—from financial services to entertainment—all while presenting ongoing challenges related to regulation, security vulnerabilities, and environmental impact.
By staying informed about these core technologies underpinning blockchains today—and future developments—you can better understand their capabilities' scope while contributing thoughtfully toward responsible adoption strategies aligned with societal needs.
Keywords: Blockchain technology components | Cryptography in blockchain | Decentralized networks | Consensus mechanisms | Proof of Work vs Proof of Stake | Blockchain security features | Environmental impact of blockchains


Lo
2025-05-14 23:08
What blockchain or technology does it use?
What Blockchain Technology Uses: An In-Depth Overview
Understanding the core technology behind blockchain is essential for grasping its potential and limitations. At its heart, blockchain employs a combination of cryptography, decentralized networks, and consensus mechanisms to create a secure and transparent digital ledger system. This foundation allows blockchain to serve as a trustworthy platform for various applications across industries.
Cryptography: Securing Transactions
Cryptography is fundamental to blockchain's security features. It involves encrypting transaction data so that only authorized parties can access or modify it. Public-key cryptography, in particular, plays a vital role by generating unique key pairs—public keys used as addresses and private keys for signing transactions. This ensures that each transaction is authentic and tamper-proof. Additionally, cryptographic hashing functions produce fixed-length strings (hashes) from data inputs; these hashes are used to link blocks securely in the chain, making alterations detectable.
Decentralized Network Architecture
Unlike traditional centralized databases managed by single entities, blockchain operates on a decentralized network of computers called nodes. Each node maintains an identical copy of the entire ledger, which promotes transparency and resilience against failures or attacks. When new transactions occur, they are broadcasted across the network where nodes validate them through consensus mechanisms before adding them to the ledger.
Consensus Mechanisms: Validating Data Integrity
Consensus algorithms ensure all participants agree on the state of the ledger without relying on central authority. The two most common methods are Proof of Work (PoW) and Proof of Stake (PoS).
- Proof of Work requires miners to solve complex mathematical puzzles—a process that consumes significant computational power—to validate transactions and add new blocks.
- Proof of Stake, on the other hand, selects validators based on their holdings or stake in the network’s cryptocurrency value rather than computational effort.
These mechanisms prevent malicious activities like double-spending or fraudulent entries by making it costly or impractical for bad actors to manipulate data.
How Blockchain Uses These Technologies in Practice
The integration of cryptography, decentralization, and consensus protocols enables blockchain's wide-ranging applications:
- In finance—facilitating secure cross-border payments with reduced costs.
- In government—tracking expenditures transparently while safeguarding sensitive information.
- In entertainment—enabling NFT ownership verification within gaming ecosystems.
- In cybersecurity—protecting critical infrastructure from cyber threats through tamper-resistant ledgers.
Each application leverages these underlying technologies differently but relies fundamentally on their combined strengths for security and trustworthiness.
Recent Innovations Related to Blockchain Protocols
Advancements continue shaping how blockchain systems operate:
- Enhanced Security Measures: Newer protocols aim at reducing vulnerabilities exposed during incidents like ransomware attacks involving educational institutions such as PowerSchool’s 2025 breach.
- Legal Developments Around NFTs: Ongoing legal battles over intellectual property rights associated with popular collections like Bored Ape Yacht Club highlight evolving regulatory landscapes affecting how blockchains handle ownership verification.
- Energy-Efficient Consensus Models: To address environmental concerns linked with PoW systems’ high energy consumption—which has garnered criticism—the industry is exploring alternatives such as Proof of Stake or hybrid models that balance security with sustainability.
These innovations demonstrate both technological progressions aimed at improving robustness while navigating emerging legal frameworks.
Addressing Challenges Through Technological Choices
Despite its strengths, blockchain faces challenges rooted in its technological design:
Regulatory uncertainty complicates widespread adoption; different jurisdictions have varying rules regarding cryptocurrencies and digital assets.
Security risks persist if implementations lack proper safeguards; incidents like ransomware breaches underscore this vulnerability despite inherent cryptographic protections.
Environmental impact remains contentious due to energy-intensive processes required by some consensus algorithms; ongoing research seeks greener solutions without compromising security standards.
By understanding these technical underpinnings—including cryptographic techniques like hashing functions & public-private key pairs—and how they interact within decentralized networks governed by specific consensus protocols—stakeholders can better evaluate both opportunities and risks associated with deploying blockchain solutions effectively.
Why It Matters for Users & Businesses
For users seeking transparency or businesses aiming for secure recordkeeping—and especially those involved in finance or digital asset management—the choice of underlying technology influences trustworthiness significantly. Knowing whether a platform uses energy-efficient proof schemes versus traditional proof-of-work helps assess sustainability alongside performance metrics such as transaction speed or scalability potential.
In summary,
Blockchain technology relies heavily on advanced cryptographic methods combined with decentralized architectures supported by various consensus mechanisms like PoW or PoS. These components work together not only to secure data but also enable innovative applications across sectors—from financial services to entertainment—all while presenting ongoing challenges related to regulation, security vulnerabilities, and environmental impact.
By staying informed about these core technologies underpinning blockchains today—and future developments—you can better understand their capabilities' scope while contributing thoughtfully toward responsible adoption strategies aligned with societal needs.
Keywords: Blockchain technology components | Cryptography in blockchain | Decentralized networks | Consensus mechanisms | Proof of Work vs Proof of Stake | Blockchain security features | Environmental impact of blockchains
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
What Is a Cold Wallet in Cryptocurrency?
A cold wallet, also known as a hardware wallet, is a physical device used to securely store cryptocurrency private keys offline. Unlike online wallets or hot wallets, which are connected to the internet and more vulnerable to cyber threats, cold wallets keep your digital assets isolated from potential hacking attempts. This separation significantly enhances security, making cold wallets an essential tool for both individual investors and institutions aiming to safeguard their cryptocurrencies.
How Do Cold Wallets Work?
Cold wallets operate by generating and storing private keys offline. These private keys are critical because they grant access to your cryptocurrencies on various blockchain networks such as Bitcoin or Ethereum. When you want to make a transaction using a cold wallet, the device typically signs the transaction internally without exposing your private key online. The signed transaction can then be transmitted through an external device or QR code scan for broadcasting onto the blockchain.
This process ensures that at no point does your private key come into contact with internet-connected devices unless explicitly authorized by you. As a result, even if your computer or smartphone is compromised by malware or hackers, your assets remain protected because the critical data stays within the secure environment of the hardware device.
Advantages of Using Cold Wallets
The primary benefit of cold wallets lies in their enhanced security features:
- Offline Storage: By keeping private keys offline, they eliminate exposure to online hacking attempts.
- Additional Security Layers: Many models incorporate PIN codes, biometric authentication (like fingerprint scans), and encryption protocols.
- Multi-Currency Support: Most modern cold wallets support multiple cryptocurrencies across different blockchain networks—allowing users to manage diverse portfolios from one device.
- User Control & Ownership: Users retain full control over their private keys without relying on third-party services like exchanges.
Furthermore, advancements in technology have made these devices more user-friendly while maintaining high-security standards—making them suitable even for beginners who prioritize asset safety.
Types of Cold Wallet Devices
Cold wallets come in various forms designed for different user needs:
- Hardware Wallets: These are dedicated physical devices such as Ledger Nano S/X and Trezor that connect via USB or Bluetooth with computers or smartphones.
- Paper Wallets: A less common option where private keys are printed on paper; however, this method carries risks related to physical damage and loss.
- Air-Gapped Devices: Specialized computers that never connect directly online but generate transactions offline before broadcasting them via secure methods.
Most users prefer hardware wallets due to their balance between security and usability—they offer robust protection while remaining relatively straightforward to operate.
Recent Trends & Developments
Over recent years, technological innovations have driven significant improvements in cold wallet solutions:
- Enhanced security protocols like multi-signature support (requiring multiple approvals for transactions) increase protection against theft.
- User interfaces have become more intuitive with features like QR code scanning for easier transaction signing.
- The market has seen increased adoption among institutional investors seeking reliable storage options amidst rising cryptocurrency valuations.
Additionally, regulatory developments worldwide have prompted manufacturers and users alike toward better compliance standards—further legitimizing these tools within broader financial ecosystems.
Risks & Challenges Associated With Cold Wallets
While offering superior security compared to hot wallets, cold storage solutions are not entirely risk-free:
Physical Loss or Damage: If you lose access to your hardware wallet or it gets damaged without proper backup procedures (such as seed phrases), recovering funds can be impossible.
Seed Phrase Security: The seed phrase—a set of words generated during setup—is crucial; if compromised or lost, it jeopardizes access permanently.
User Error & Lack of Knowledge: Many users underestimate best practices around securing seed phrases or handling transactions securely; this can lead to vulnerabilities despite having advanced hardware devices installed.
Therefore, comprehensive user education remains vital when adopting cold storage methods—understanding how best practices mitigate potential pitfalls is essential for maximizing asset safety.
Historical Milestones in Hardware Cryptocurrency Storage
The evolution of hardware crypto storage began with pioneering products like Ledger's first model introduced in 2011 by Jean-François Thiriet—a significant milestone marking mainstream acceptance of physical crypto safes. In 2014 came Satoshi Labs' Trezor wallet—a notable competitor offering open-source design principles emphasizing transparency and trustworthiness.
The COVID pandemic accelerated adoption trends around 2020 when increased digital asset interest coincided with heightened concerns about cybersecurity threats during remote work periods. By 2022 onwards—with growing institutional involvement—the market experienced rapid growth fueled by demand for secure custody solutions tailored toward larger holdings beyond individual retail investors.
Why Are Cold Wallets Important Today?
As cryptocurrencies become increasingly mainstream—and their values rise—the importance of secure storage cannot be overstated. Hot wallets may offer convenience but expose assets unnecessarily; thus many prefer moving large holdings into physically isolated environments provided by hardware devices known as cold wallets.
Moreover—and crucially—the ongoing development within this space aims at balancing ease-of-use with maximum protection through innovative features like multi-signature setups and biometric authentication systems—all designed under rigorous industry standards aligned with evolving regulatory frameworks.
Best Practices For Using Cold Wallets Effectively
To maximize security benefits when using a cold wallet:
- Always generate seed phrases securely—preferably offline—and store them safely away from prying eyes.
- Avoid sharing sensitive information related to your device publicly—even on social media platforms—to prevent targeted attacks.
- Keep firmware updated regularly according to manufacturer instructions—to patch vulnerabilities promptly.
- Use multi-factor authentication where available—for example: combining PIN codes with biometric verification—to add layers against unauthorized access
- Consider employing multi-signature arrangements if managing large sums—that require multiple approvals before executing transactions.
Final Thoughts
Cold wallets represent one of the most effective means available today for safeguarding digital assets against cyber threats inherent in today's interconnected world — especially given increasing market volatility alongside rising institutional interest . While they require careful handling—including safeguarding seed phrases—they provide peace-of-mind through robust offline protection mechanisms rooted deeply within trusted technology standards developed over years since early innovations like Ledger’s debut back in 2011.
By understanding how these devices work—and following best practices—you can significantly reduce risks associated with storing cryptocurrencies while maintaining full control over your investments’ security profile.


Lo
2025-05-15 00:44
What is a cold wallet?
What Is a Cold Wallet in Cryptocurrency?
A cold wallet, also known as a hardware wallet, is a physical device used to securely store cryptocurrency private keys offline. Unlike online wallets or hot wallets, which are connected to the internet and more vulnerable to cyber threats, cold wallets keep your digital assets isolated from potential hacking attempts. This separation significantly enhances security, making cold wallets an essential tool for both individual investors and institutions aiming to safeguard their cryptocurrencies.
How Do Cold Wallets Work?
Cold wallets operate by generating and storing private keys offline. These private keys are critical because they grant access to your cryptocurrencies on various blockchain networks such as Bitcoin or Ethereum. When you want to make a transaction using a cold wallet, the device typically signs the transaction internally without exposing your private key online. The signed transaction can then be transmitted through an external device or QR code scan for broadcasting onto the blockchain.
This process ensures that at no point does your private key come into contact with internet-connected devices unless explicitly authorized by you. As a result, even if your computer or smartphone is compromised by malware or hackers, your assets remain protected because the critical data stays within the secure environment of the hardware device.
Advantages of Using Cold Wallets
The primary benefit of cold wallets lies in their enhanced security features:
- Offline Storage: By keeping private keys offline, they eliminate exposure to online hacking attempts.
- Additional Security Layers: Many models incorporate PIN codes, biometric authentication (like fingerprint scans), and encryption protocols.
- Multi-Currency Support: Most modern cold wallets support multiple cryptocurrencies across different blockchain networks—allowing users to manage diverse portfolios from one device.
- User Control & Ownership: Users retain full control over their private keys without relying on third-party services like exchanges.
Furthermore, advancements in technology have made these devices more user-friendly while maintaining high-security standards—making them suitable even for beginners who prioritize asset safety.
Types of Cold Wallet Devices
Cold wallets come in various forms designed for different user needs:
- Hardware Wallets: These are dedicated physical devices such as Ledger Nano S/X and Trezor that connect via USB or Bluetooth with computers or smartphones.
- Paper Wallets: A less common option where private keys are printed on paper; however, this method carries risks related to physical damage and loss.
- Air-Gapped Devices: Specialized computers that never connect directly online but generate transactions offline before broadcasting them via secure methods.
Most users prefer hardware wallets due to their balance between security and usability—they offer robust protection while remaining relatively straightforward to operate.
Recent Trends & Developments
Over recent years, technological innovations have driven significant improvements in cold wallet solutions:
- Enhanced security protocols like multi-signature support (requiring multiple approvals for transactions) increase protection against theft.
- User interfaces have become more intuitive with features like QR code scanning for easier transaction signing.
- The market has seen increased adoption among institutional investors seeking reliable storage options amidst rising cryptocurrency valuations.
Additionally, regulatory developments worldwide have prompted manufacturers and users alike toward better compliance standards—further legitimizing these tools within broader financial ecosystems.
Risks & Challenges Associated With Cold Wallets
While offering superior security compared to hot wallets, cold storage solutions are not entirely risk-free:
Physical Loss or Damage: If you lose access to your hardware wallet or it gets damaged without proper backup procedures (such as seed phrases), recovering funds can be impossible.
Seed Phrase Security: The seed phrase—a set of words generated during setup—is crucial; if compromised or lost, it jeopardizes access permanently.
User Error & Lack of Knowledge: Many users underestimate best practices around securing seed phrases or handling transactions securely; this can lead to vulnerabilities despite having advanced hardware devices installed.
Therefore, comprehensive user education remains vital when adopting cold storage methods—understanding how best practices mitigate potential pitfalls is essential for maximizing asset safety.
Historical Milestones in Hardware Cryptocurrency Storage
The evolution of hardware crypto storage began with pioneering products like Ledger's first model introduced in 2011 by Jean-François Thiriet—a significant milestone marking mainstream acceptance of physical crypto safes. In 2014 came Satoshi Labs' Trezor wallet—a notable competitor offering open-source design principles emphasizing transparency and trustworthiness.
The COVID pandemic accelerated adoption trends around 2020 when increased digital asset interest coincided with heightened concerns about cybersecurity threats during remote work periods. By 2022 onwards—with growing institutional involvement—the market experienced rapid growth fueled by demand for secure custody solutions tailored toward larger holdings beyond individual retail investors.
Why Are Cold Wallets Important Today?
As cryptocurrencies become increasingly mainstream—and their values rise—the importance of secure storage cannot be overstated. Hot wallets may offer convenience but expose assets unnecessarily; thus many prefer moving large holdings into physically isolated environments provided by hardware devices known as cold wallets.
Moreover—and crucially—the ongoing development within this space aims at balancing ease-of-use with maximum protection through innovative features like multi-signature setups and biometric authentication systems—all designed under rigorous industry standards aligned with evolving regulatory frameworks.
Best Practices For Using Cold Wallets Effectively
To maximize security benefits when using a cold wallet:
- Always generate seed phrases securely—preferably offline—and store them safely away from prying eyes.
- Avoid sharing sensitive information related to your device publicly—even on social media platforms—to prevent targeted attacks.
- Keep firmware updated regularly according to manufacturer instructions—to patch vulnerabilities promptly.
- Use multi-factor authentication where available—for example: combining PIN codes with biometric verification—to add layers against unauthorized access
- Consider employing multi-signature arrangements if managing large sums—that require multiple approvals before executing transactions.
Final Thoughts
Cold wallets represent one of the most effective means available today for safeguarding digital assets against cyber threats inherent in today's interconnected world — especially given increasing market volatility alongside rising institutional interest . While they require careful handling—including safeguarding seed phrases—they provide peace-of-mind through robust offline protection mechanisms rooted deeply within trusted technology standards developed over years since early innovations like Ledger’s debut back in 2011.
By understanding how these devices work—and following best practices—you can significantly reduce risks associated with storing cryptocurrencies while maintaining full control over your investments’ security profile.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
What is the Difference Between Hot Wallets and Cold Wallets in Cryptocurrency?
Understanding the fundamental differences between hot wallets and cold wallets is essential for anyone involved in cryptocurrency trading, investing, or long-term holding. As digital assets become more mainstream, security remains a top concern. Choosing the right storage method depends on your individual needs, risk tolerance, and how actively you manage your cryptocurrencies.
Hot Wallets: Convenience Meets Risk
Hot wallets are digital wallets connected to the internet. They are typically software-based applications accessible via smartphones or web platforms. Because of their online nature, hot wallets offer unmatched convenience for users who frequently buy, sell, or transfer cryptocurrencies.
The primary advantage of hot wallets lies in their ease of use. Transactions can be completed swiftly without cumbersome manual steps—ideal for day traders or those making regular transactions. Their user-friendly interfaces simplify managing multiple cryptocurrencies and enable quick access to funds whenever needed.
However, this convenience comes with notable security risks. Being constantly connected to the internet makes hot wallets vulnerable to hacking attempts and cyber attacks. High-profile breaches have demonstrated that malicious actors can exploit vulnerabilities in these platforms to steal funds if proper security measures aren’t implemented.
For most casual users or those engaging in frequent trading activities, hot wallets provide a practical solution but should be used with caution—preferably with additional layers of security like two-factor authentication (2FA) and strong passwords.
Cold Wallets: Security-Focused Storage
In contrast to hot wallets, cold wallets are physical devices designed specifically for offline storage of private keys—the critical credentials needed to access cryptocurrency holdings. Hardware cold wallets store private keys securely away from internet exposure; they require manual intervention (such as connecting via USB) when initiating transactions.
The main benefit of cold storage is its enhanced security profile. Offline operation significantly reduces vulnerability to hacking since there’s no direct online connection that could be exploited remotely by cybercriminals. This makes cold wallets especially suitable for long-term investors who want maximum protection against theft or loss over time.
Additionally, owning a hardware wallet gives users full control over their private keys without relying on third-party custodians—a key aspect aligned with principles of decentralization and self-sovereignty common within crypto communities.
Despite these advantages, cold storage has some drawbacks: it’s less convenient than hot options because transactions involve extra steps like connecting devices manually; also, hardware devices come at a higher cost compared to free software solutions associated with hot wallets.
Recent Trends & Developments
Over recent years, there has been a noticeable shift toward increased adoption of hardware (cold) wallet solutions among both retail investors and institutional players concerned about asset security amid rising cyber threats. Manufacturers have responded by integrating advanced features such as multi-signature requirements—where multiple approvals are necessary before executing transactions—and sophisticated encryption protocols that bolster defenses against potential breaches.
Regulatory scrutiny around cryptocurrency custody practices is intensifying globally as authorities seek ways to protect consumers while fostering innovation within blockchain technology sectors. These regulatory developments may influence user preferences toward more secure options like hardware-based cold storage solutions due to compliance pressures or mandated safeguards.
Furthermore, educational efforts aimed at raising awareness about different wallet types help users make informed decisions aligned with their risk profiles—highlighting that no single solution fits all circumstances but rather depends on individual goals and operational needs.
Potential Impacts & Future Outlook
As awareness around cybersecurity risks grows among crypto holders—including high-profile exchange hacks—the demand for secure offline storage methods continues rising sharply. This trend suggests an increasing preference for hardware (cold) solutions among serious investors seeking peace of mind over long-term holdings rather than frequent trading activity requiring rapid access through hot wallets.
Regulators’ focus on establishing clear guidelines around custody standards might further encourage adoption of secure storage practices—potentially leading exchanges and service providers alike toward integrating more robust safety features into their offerings while educating clients about best practices in safeguarding digital assets effectively.
Meanwhile, improvements within hot wallet technology aim at balancing convenience with enhanced security measures such as multi-factor authentication systems or biometric protections—all designed so users can enjoy quick transaction speeds without compromising safety standards.
Ultimately,
selecting between a hot wallet versus a cold wallet hinges upon understanding personal priorities: whether prioritizing ease-of-use versus maximum protection—and recognizing that combining both approaches often provides an optimal balance depending on asset size and intended use case.
Why It Matters for Crypto Users
Choosing appropriate cryptocurrency storage methods directly impacts asset safety amid evolving threats from hackers targeting digital currencies worldwide. Hot wallets serve well during active trading phases but should not hold large sums long term unless supplemented by additional protective layers; conversely,
cold storages excel at safeguarding substantial holdings over extended periods but require patience during transaction processes.
Educating oneself about these distinctions empowers crypto enthusiasts—from beginners learning about basic concepts all the way up to seasoned traders managing significant portfolios—to make smarter decisions aligned with best practices endorsed by cybersecurity experts.
Key Takeaways:
- Hot Wallets provide quick access but pose higher cybersecurity risks due to constant internet connectivity.
- Cold Wallets offer superior protection through offline operation but involve higher costs and less immediacy.
- Recent innovations focus on enhancing security features across both types while regulatory trends push towards safer custody solutions.
- Combining both methods based on specific needs often yields optimal results—for example,using warm/hot options for daily trades alongside secure cold vaults for long-term savings.
By understanding these core differences—and staying informed about ongoing technological advancements—you can better safeguard your digital assets against theft while maintaining flexibility suited precisely to your investment strategy.
Semantic & LSI Keywords:
cryptocurrency safekeeping | crypto wallet comparison | hardware vs software crypto wallet | best way to store Bitcoin | blockchain asset management | secure crypto storage | private key management | cryptocurrency investment safety


Lo
2025-05-14 07:13
What is the difference between hot wallets and cold wallets?
What is the Difference Between Hot Wallets and Cold Wallets in Cryptocurrency?
Understanding the fundamental differences between hot wallets and cold wallets is essential for anyone involved in cryptocurrency trading, investing, or long-term holding. As digital assets become more mainstream, security remains a top concern. Choosing the right storage method depends on your individual needs, risk tolerance, and how actively you manage your cryptocurrencies.
Hot Wallets: Convenience Meets Risk
Hot wallets are digital wallets connected to the internet. They are typically software-based applications accessible via smartphones or web platforms. Because of their online nature, hot wallets offer unmatched convenience for users who frequently buy, sell, or transfer cryptocurrencies.
The primary advantage of hot wallets lies in their ease of use. Transactions can be completed swiftly without cumbersome manual steps—ideal for day traders or those making regular transactions. Their user-friendly interfaces simplify managing multiple cryptocurrencies and enable quick access to funds whenever needed.
However, this convenience comes with notable security risks. Being constantly connected to the internet makes hot wallets vulnerable to hacking attempts and cyber attacks. High-profile breaches have demonstrated that malicious actors can exploit vulnerabilities in these platforms to steal funds if proper security measures aren’t implemented.
For most casual users or those engaging in frequent trading activities, hot wallets provide a practical solution but should be used with caution—preferably with additional layers of security like two-factor authentication (2FA) and strong passwords.
Cold Wallets: Security-Focused Storage
In contrast to hot wallets, cold wallets are physical devices designed specifically for offline storage of private keys—the critical credentials needed to access cryptocurrency holdings. Hardware cold wallets store private keys securely away from internet exposure; they require manual intervention (such as connecting via USB) when initiating transactions.
The main benefit of cold storage is its enhanced security profile. Offline operation significantly reduces vulnerability to hacking since there’s no direct online connection that could be exploited remotely by cybercriminals. This makes cold wallets especially suitable for long-term investors who want maximum protection against theft or loss over time.
Additionally, owning a hardware wallet gives users full control over their private keys without relying on third-party custodians—a key aspect aligned with principles of decentralization and self-sovereignty common within crypto communities.
Despite these advantages, cold storage has some drawbacks: it’s less convenient than hot options because transactions involve extra steps like connecting devices manually; also, hardware devices come at a higher cost compared to free software solutions associated with hot wallets.
Recent Trends & Developments
Over recent years, there has been a noticeable shift toward increased adoption of hardware (cold) wallet solutions among both retail investors and institutional players concerned about asset security amid rising cyber threats. Manufacturers have responded by integrating advanced features such as multi-signature requirements—where multiple approvals are necessary before executing transactions—and sophisticated encryption protocols that bolster defenses against potential breaches.
Regulatory scrutiny around cryptocurrency custody practices is intensifying globally as authorities seek ways to protect consumers while fostering innovation within blockchain technology sectors. These regulatory developments may influence user preferences toward more secure options like hardware-based cold storage solutions due to compliance pressures or mandated safeguards.
Furthermore, educational efforts aimed at raising awareness about different wallet types help users make informed decisions aligned with their risk profiles—highlighting that no single solution fits all circumstances but rather depends on individual goals and operational needs.
Potential Impacts & Future Outlook
As awareness around cybersecurity risks grows among crypto holders—including high-profile exchange hacks—the demand for secure offline storage methods continues rising sharply. This trend suggests an increasing preference for hardware (cold) solutions among serious investors seeking peace of mind over long-term holdings rather than frequent trading activity requiring rapid access through hot wallets.
Regulators’ focus on establishing clear guidelines around custody standards might further encourage adoption of secure storage practices—potentially leading exchanges and service providers alike toward integrating more robust safety features into their offerings while educating clients about best practices in safeguarding digital assets effectively.
Meanwhile, improvements within hot wallet technology aim at balancing convenience with enhanced security measures such as multi-factor authentication systems or biometric protections—all designed so users can enjoy quick transaction speeds without compromising safety standards.
Ultimately,
selecting between a hot wallet versus a cold wallet hinges upon understanding personal priorities: whether prioritizing ease-of-use versus maximum protection—and recognizing that combining both approaches often provides an optimal balance depending on asset size and intended use case.
Why It Matters for Crypto Users
Choosing appropriate cryptocurrency storage methods directly impacts asset safety amid evolving threats from hackers targeting digital currencies worldwide. Hot wallets serve well during active trading phases but should not hold large sums long term unless supplemented by additional protective layers; conversely,
cold storages excel at safeguarding substantial holdings over extended periods but require patience during transaction processes.
Educating oneself about these distinctions empowers crypto enthusiasts—from beginners learning about basic concepts all the way up to seasoned traders managing significant portfolios—to make smarter decisions aligned with best practices endorsed by cybersecurity experts.
Key Takeaways:
- Hot Wallets provide quick access but pose higher cybersecurity risks due to constant internet connectivity.
- Cold Wallets offer superior protection through offline operation but involve higher costs and less immediacy.
- Recent innovations focus on enhancing security features across both types while regulatory trends push towards safer custody solutions.
- Combining both methods based on specific needs often yields optimal results—for example,using warm/hot options for daily trades alongside secure cold vaults for long-term savings.
By understanding these core differences—and staying informed about ongoing technological advancements—you can better safeguard your digital assets against theft while maintaining flexibility suited precisely to your investment strategy.
Semantic & LSI Keywords:
cryptocurrency safekeeping | crypto wallet comparison | hardware vs software crypto wallet | best way to store Bitcoin | blockchain asset management | secure crypto storage | private key management | cryptocurrency investment safety
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
MicroStrategy trade autour de 337 $ après avoir cassé son support. 👀 Prochain stop : zone de demande 300–315 $.
📊 Scénarios possibles : ✅ Si ça tient → rebond vers 360 $ 🚀 ❌ Si ça casse → chute plus profonde vers 230–250 $ ⚠️
👉 Croyez-vous à un rebond rapide ou à une correction prolongée pour $MSTR ?
#MSTR #BitcoinStocks #CryptoMarkets
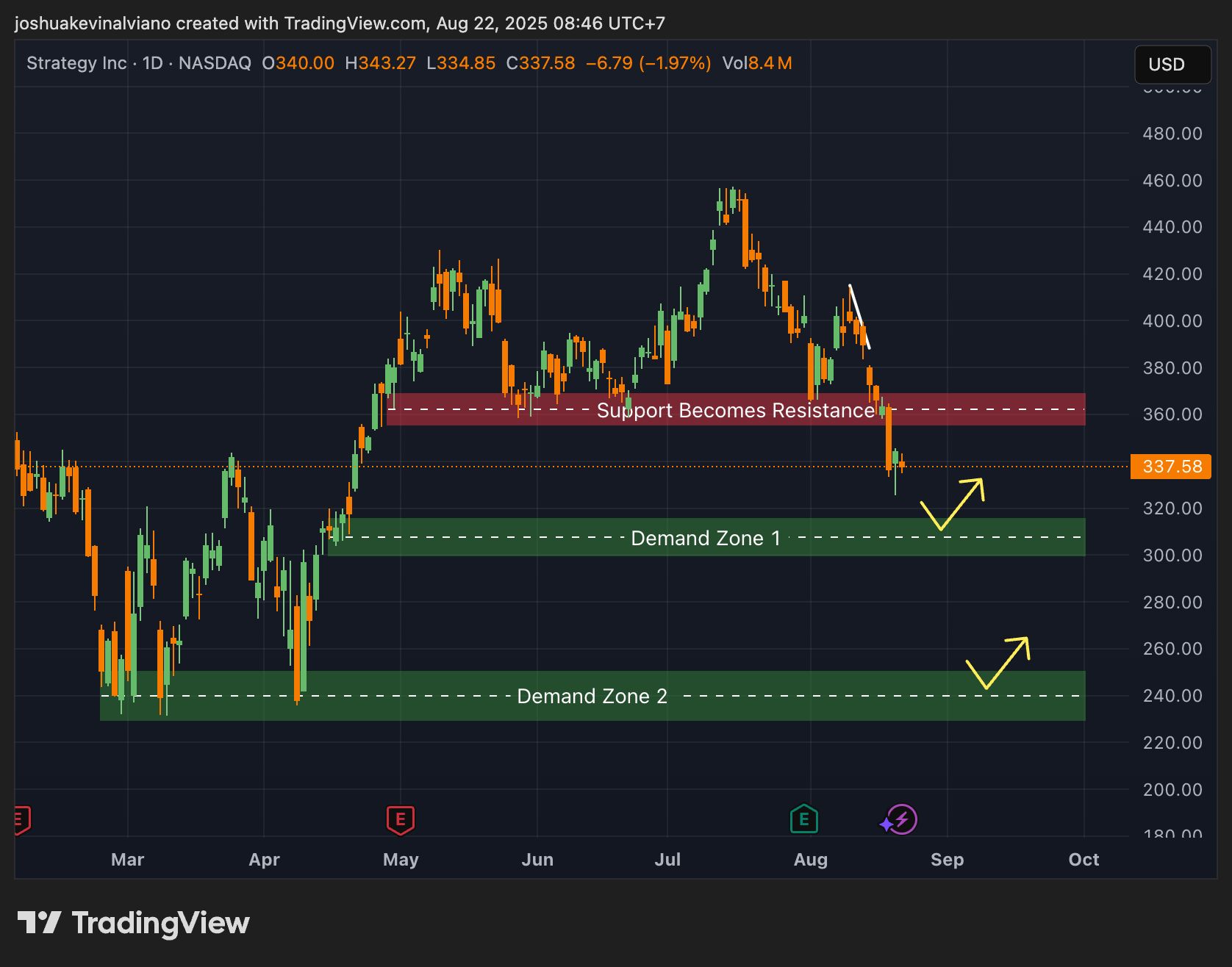


Carmelita
2025-08-22 11:48
$MSTR sous pression : le test décisif approche !
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Insurance Options for Protecting Crypto Holdings
Cryptocurrency has revolutionized the financial landscape, offering new opportunities for investment and wealth creation. However, the decentralized and highly volatile nature of digital assets introduces unique risks that require specialized protection measures. As more individuals and institutions hold significant amounts of cryptocurrencies, the demand for effective insurance options has surged. This article explores the current landscape of crypto insurance, including available products, key providers, recent developments, challenges faced by the industry, and future trends.
Understanding Crypto Risks and Why Insurance Is Necessary
Cryptocurrencies are susceptible to various risks that can threaten investors’ holdings. Cybersecurity threats such as hacking incidents have resulted in substantial losses for many holders. Physical theft remains a concern despite digital security measures—especially when private keys or hardware wallets are compromised or stolen. Market volatility also poses a risk; sudden price swings can lead to significant financial losses within short periods.
Moreover, regulatory uncertainty adds another layer of complexity. Different jurisdictions have varying rules regarding cryptocurrency operations and insurance coverage applicability. This ambiguity can leave investors exposed to legal risks or prevent them from accessing certain types of coverage altogether.
Given these factors, crypto-specific insurance products aim to mitigate these vulnerabilities by providing financial protection against specific threats like hacking or theft while addressing market-related risks through tailored policies.
Types of Cryptocurrency Insurance Available Today
The spectrum of crypto insurance is diverse but still evolving compared to traditional finance sectors. The primary categories include:
- Hacker Insurance: Covers losses resulting from cyber attacks targeting exchanges or individual wallets.
- Theft Insurance: Protects against physical thefts involving hardware wallets or custodial services.
- Market Volatility Insurance: Offers coverage for sudden market downturns that cause substantial asset devaluation.
- Regulatory Compliance Insurance: Addresses legal risks associated with changing regulations impacting cryptocurrency operations.
Each type caters to different risk profiles and investor needs—ranging from retail traders safeguarding their personal holdings to institutional investors managing large portfolios requiring comprehensive coverage solutions.
Leading Providers in Crypto Insurance Sector
Several companies have emerged as key players offering various forms of cryptocurrency insurance:
- Nexo: Provides a suite of products including hacker and theft protections aimed at both individual users and institutional clients.
- Coincover: Specializes in insuring against hacking incidents and physical thefts with partnerships across multiple platforms.
- BitGo: Known for its multi-signature wallet technology combined with integrated insurance policies designed specifically for high-net-worth clients.
- Swiss Re: A global reinsurer that has recently entered the crypto space by launching specialized policies targeted at institutional investors seeking robust risk management tools.
These providers leverage advanced cybersecurity protocols alongside traditional underwriting practices adapted for blockchain assets—aiming to build trust within an industry still grappling with skepticism about insurability.
Recent Developments Shaping Crypto Insurance
The industry’s rapid growth is reflected in several notable developments over recent years:
- In 2023, Nexo launched its "Nexo Insurance" product focusing on covering hacking attempts and cyber breaches affecting user funds.
- By 2024, Coincover announced strategic partnerships with major cryptocurrency exchanges—making their insurance services more accessible directly through trading platforms.
- In 2025, Swiss Re introduced tailored policies designed explicitly for institutional clients involved in large-scale crypto investments—highlighting increasing acceptance among traditional insurers into this niche market.
These innovations demonstrate how insurers are adapting their offerings based on emerging needs while leveraging technological advancements like blockchain security enhancements to reduce reliance solely on external protections.
Challenges Facing the Crypto Insurance Industry
Despite promising growth prospects, several hurdles hinder widespread adoption:
Regulatory Uncertainty
Lack of clear regulatory frameworks complicates policy development; insurers often face legal ambiguities regarding what constitutes insurable events within different jurisdictions—a situation that could lead to disputes over claims payouts or even restrict product offerings altogether.
Market Volatility
Crypto’s inherent price swings challenge actuarial models used by insurers—they must balance affordability with sufficient reserves without exposing themselves excessively during downturns which could threaten financial stability if claims spike unexpectedly.
Cybersecurity Risks
As cybercriminal tactics evolve rapidly—with increasingly sophisticated attacks—the threat landscape expands continuously; this dynamic environment makes it difficult for insurers to accurately assess risk levels or develop comprehensive coverage terms without frequent updates.
Data Collection Difficulties
Decentralization means transaction data is dispersed across numerous nodes without centralized oversight—a barrier when trying to quantify exposure levels accurately necessary for underwriting processes effectively.
Reputation Concerns
Insurers face reputational damage if they fail on claim settlements due either technical issues or insufficient reserves—which could undermine confidence among potential customers considering purchasing crypto-specific policies.
Future Trends in Cryptocurrency Risk Management & Protection
Looking ahead, several trends are poised to shape how cryptocurrencies will be insured moving forward:
- Increased Adoption: As mainstream institutions continue integrating cryptocurrencies into their portfolios—including hedge funds & family offices—the demand for reliable protection mechanisms will grow exponentially.
- Product Innovation: Insurers are expected not only to expand existing offerings but also develop new solutions such as parametric coverages triggered automatically upon predefined events (e.g., exchange hacks) providing faster payouts.
- Enhanced Security Technologies: Blockchain advancements like multi-party computation (MPC) keys & decentralized custody solutions will reduce some reliance on traditional insurance by improving asset security inherently.
- Regulatory Clarity: Governments worldwide are gradually establishing clearer guidelines around digital assets—which will facilitate standardized policy frameworks fostering trustworthiness among consumers & providers alike.
- Integration With Traditional Finance: Combining crypto-specific protections within broader financial planning tools aims at creating holistic risk management strategies suitable both online & offline environments.
Navigating Crypto Asset Protection Effectively
For individuals holding cryptocurrencies—or institutions managing large digital asset portfolios—it’s crucial not only to understand available options but also assess which best align with your specific needs considering your risk appetite—and stay informed about ongoing industry changes that might impact your coverage choices.
By leveraging specialized insurer offerings alongside robust cybersecurity practices—including cold storage solutions—and staying compliant with evolving regulations—you can significantly mitigate potential losses associated with your digital investments while contributing toward building greater trustworthiness within this emerging sector.


kai
2025-05-22 03:09
What insurance options exist for protecting crypto holdings?
Insurance Options for Protecting Crypto Holdings
Cryptocurrency has revolutionized the financial landscape, offering new opportunities for investment and wealth creation. However, the decentralized and highly volatile nature of digital assets introduces unique risks that require specialized protection measures. As more individuals and institutions hold significant amounts of cryptocurrencies, the demand for effective insurance options has surged. This article explores the current landscape of crypto insurance, including available products, key providers, recent developments, challenges faced by the industry, and future trends.
Understanding Crypto Risks and Why Insurance Is Necessary
Cryptocurrencies are susceptible to various risks that can threaten investors’ holdings. Cybersecurity threats such as hacking incidents have resulted in substantial losses for many holders. Physical theft remains a concern despite digital security measures—especially when private keys or hardware wallets are compromised or stolen. Market volatility also poses a risk; sudden price swings can lead to significant financial losses within short periods.
Moreover, regulatory uncertainty adds another layer of complexity. Different jurisdictions have varying rules regarding cryptocurrency operations and insurance coverage applicability. This ambiguity can leave investors exposed to legal risks or prevent them from accessing certain types of coverage altogether.
Given these factors, crypto-specific insurance products aim to mitigate these vulnerabilities by providing financial protection against specific threats like hacking or theft while addressing market-related risks through tailored policies.
Types of Cryptocurrency Insurance Available Today
The spectrum of crypto insurance is diverse but still evolving compared to traditional finance sectors. The primary categories include:
- Hacker Insurance: Covers losses resulting from cyber attacks targeting exchanges or individual wallets.
- Theft Insurance: Protects against physical thefts involving hardware wallets or custodial services.
- Market Volatility Insurance: Offers coverage for sudden market downturns that cause substantial asset devaluation.
- Regulatory Compliance Insurance: Addresses legal risks associated with changing regulations impacting cryptocurrency operations.
Each type caters to different risk profiles and investor needs—ranging from retail traders safeguarding their personal holdings to institutional investors managing large portfolios requiring comprehensive coverage solutions.
Leading Providers in Crypto Insurance Sector
Several companies have emerged as key players offering various forms of cryptocurrency insurance:
- Nexo: Provides a suite of products including hacker and theft protections aimed at both individual users and institutional clients.
- Coincover: Specializes in insuring against hacking incidents and physical thefts with partnerships across multiple platforms.
- BitGo: Known for its multi-signature wallet technology combined with integrated insurance policies designed specifically for high-net-worth clients.
- Swiss Re: A global reinsurer that has recently entered the crypto space by launching specialized policies targeted at institutional investors seeking robust risk management tools.
These providers leverage advanced cybersecurity protocols alongside traditional underwriting practices adapted for blockchain assets—aiming to build trust within an industry still grappling with skepticism about insurability.
Recent Developments Shaping Crypto Insurance
The industry’s rapid growth is reflected in several notable developments over recent years:
- In 2023, Nexo launched its "Nexo Insurance" product focusing on covering hacking attempts and cyber breaches affecting user funds.
- By 2024, Coincover announced strategic partnerships with major cryptocurrency exchanges—making their insurance services more accessible directly through trading platforms.
- In 2025, Swiss Re introduced tailored policies designed explicitly for institutional clients involved in large-scale crypto investments—highlighting increasing acceptance among traditional insurers into this niche market.
These innovations demonstrate how insurers are adapting their offerings based on emerging needs while leveraging technological advancements like blockchain security enhancements to reduce reliance solely on external protections.
Challenges Facing the Crypto Insurance Industry
Despite promising growth prospects, several hurdles hinder widespread adoption:
Regulatory Uncertainty
Lack of clear regulatory frameworks complicates policy development; insurers often face legal ambiguities regarding what constitutes insurable events within different jurisdictions—a situation that could lead to disputes over claims payouts or even restrict product offerings altogether.
Market Volatility
Crypto’s inherent price swings challenge actuarial models used by insurers—they must balance affordability with sufficient reserves without exposing themselves excessively during downturns which could threaten financial stability if claims spike unexpectedly.
Cybersecurity Risks
As cybercriminal tactics evolve rapidly—with increasingly sophisticated attacks—the threat landscape expands continuously; this dynamic environment makes it difficult for insurers to accurately assess risk levels or develop comprehensive coverage terms without frequent updates.
Data Collection Difficulties
Decentralization means transaction data is dispersed across numerous nodes without centralized oversight—a barrier when trying to quantify exposure levels accurately necessary for underwriting processes effectively.
Reputation Concerns
Insurers face reputational damage if they fail on claim settlements due either technical issues or insufficient reserves—which could undermine confidence among potential customers considering purchasing crypto-specific policies.
Future Trends in Cryptocurrency Risk Management & Protection
Looking ahead, several trends are poised to shape how cryptocurrencies will be insured moving forward:
- Increased Adoption: As mainstream institutions continue integrating cryptocurrencies into their portfolios—including hedge funds & family offices—the demand for reliable protection mechanisms will grow exponentially.
- Product Innovation: Insurers are expected not only to expand existing offerings but also develop new solutions such as parametric coverages triggered automatically upon predefined events (e.g., exchange hacks) providing faster payouts.
- Enhanced Security Technologies: Blockchain advancements like multi-party computation (MPC) keys & decentralized custody solutions will reduce some reliance on traditional insurance by improving asset security inherently.
- Regulatory Clarity: Governments worldwide are gradually establishing clearer guidelines around digital assets—which will facilitate standardized policy frameworks fostering trustworthiness among consumers & providers alike.
- Integration With Traditional Finance: Combining crypto-specific protections within broader financial planning tools aims at creating holistic risk management strategies suitable both online & offline environments.
Navigating Crypto Asset Protection Effectively
For individuals holding cryptocurrencies—or institutions managing large digital asset portfolios—it’s crucial not only to understand available options but also assess which best align with your specific needs considering your risk appetite—and stay informed about ongoing industry changes that might impact your coverage choices.
By leveraging specialized insurer offerings alongside robust cybersecurity practices—including cold storage solutions—and staying compliant with evolving regulations—you can significantly mitigate potential losses associated with your digital investments while contributing toward building greater trustworthiness within this emerging sector.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
What's Shown on the Price Axis? A Guide to Financial Data Visualization and Market Trends
Understanding what is displayed on the price axis is essential for anyone involved in financial markets, whether you're an investor, analyst, or enthusiast. The price axis serves as a visual tool that helps interpret market movements, identify trends, and make informed decisions. This article explores the core elements of the price axis in data visualization, its significance across different markets—including cryptocurrencies—and recent developments shaping how prices are represented.
What Is the Price Axis in Financial Charts?
The price axis is a fundamental component of financial charts that visually represents an asset's value over time. It typically appears as a vertical line or scale alongside horizontal axes representing time intervals. By plotting asset prices—such as stocks, cryptocurrencies, commodities—on this axis, traders and analysts can quickly grasp how values fluctuate within specific periods.
In practical terms, when you look at a candlestick chart for Bitcoin or a line graph for stock prices, the vertical scale indicates how much each asset costs at any given point. This visual cue allows users to detect upward or downward trends swiftly and assess market momentum.
Types of Charts That Use the Price Axis
Different chart types utilize the price axis to convey various aspects of market behavior:
- Line Graphs: These connect closing prices over time with continuous lines to highlight overall trends.
- Candlestick Charts: Offering detailed insights into daily trading activity by displaying open, high, low, and close prices within each period.
- Bar Charts: Similar to candlesticks but with bars representing high-low ranges; often used for volume analysis combined with pricing data.
Each chart type provides unique advantages depending on analytical needs—from simple trend identification to detailed pattern recognition.
The Role of Price Axis in Market Analysis
The primary purpose of displaying asset prices visually is to facilitate market analysis. Investors use these charts to identify patterns such as head-and-shoulders formations or support/resistance levels that signal potential reversals or continuations. Recognizing these patterns helps inform buy/sell decisions and manage risk effectively.
Furthermore, analyzing how prices move relative to technical indicators like moving averages or RSI (Relative Strength Index) enhances decision-making accuracy. For example: if Bitcoin's price crosses above its 50-day moving average on a candlestick chart—a signal often interpreted as bullish—it can prompt investors toward buying opportunities.
Cryptocurrency Markets: Volatility Reflected on the Price Axis
Cryptocurrencies have gained prominence partly because their high volatility makes their price movements highly visible on charts. Digital assets like Bitcoin (BTC) and Ethereum (ETH) experience rapid swings driven by factors such as regulatory news or technological updates.
Recent years have seen dramatic shifts—for instance:
- Bitcoin reaching all-time highs near $65K in 2021
- Sharp declines following regulatory crackdowns or macroeconomic shifts
These fluctuations are vividly captured through changes along the cryptocurrency’s price axis—highlighting both risks and opportunities inherent in digital assets.
How Central Bank Policies Influence Prices Displayed on Charts
Monetary policies enacted by central banks significantly impact financial markets' pricing dynamics:
Interest Rate Changes: When central banks like Federal Reserve raise rates—or cut them—it influences borrowing costs affecting stock valuations and currency strength.
Quantitative Easing (QE): Large-scale asset purchases tend to increase liquidity which can inflate asset prices shown along respective axes.
For example: A series of rate hikes might lead investors away from equities into safer assets like bonds; this shift manifests clearly through declining stock prices plotted against time on charts’ axes.
Technological Innovations Impacting How Prices Are Visualized
Advances in blockchain technology have introduced new assets such as NFTs (non-fungible tokens) and DeFi tokens whose values are tracked similarly via specialized charts featuring their own unique behaviors:
- Rapidly changing NFT valuations
- DeFi token yields fluctuating based on protocol performance
Additionally, sophisticated visualization platforms like TradingView enable overlaying multiple technical indicators onto these axes—such as Bollinger Bands or Fibonacci retracements—to refine analysis further.
Regulatory Environment’s Effect on Asset Pricing Representation
Regulatory developments influence not only actual asset values but also how they are perceived visually:
- Introduction of stablecoins has provided more stability within crypto markets
- Crackdowns may cause sudden drops visible immediately along the chart’s vertical scale
Investors monitor these regulatory signals closely since they directly affect confidence levels reflected through sharp movements along both traditional financial instruments’ axes and emerging digital assets' graphs.
Risks That Can Cause Sudden Changes Along The Price Axis
Market sentiment plays a crucial role; positive news about an investment sector can trigger rapid upward spikes while negative headlines may lead swiftly into declines—all visibly represented through steep slopes or gaps in charts:
- Investor sentiment shifts
- Market manipulation tactics especially prevalent among less regulated crypto exchanges
- Broader economic downturns leading investors toward safer havens
Technological risks such as hacking incidents also contribute unpredictability—causing abrupt drops reflected instantly across relevant graphs’ scales.
Why Understanding What Is Shown On The Price Axis Matters
Grasping what information is conveyed through these visual tools enables better risk management and strategic planning. Whether tracking volatile cryptocurrencies during turbulent times—or assessing traditional stocks amid economic uncertainty—the ability to interpret changes accurately empowers smarter investment choices.
By staying informed about recent trends—including technological innovations influencing data visualization—and understanding external factors like policy shifts—you position yourself advantageously within dynamic markets where every movement along that critical vertical scale counts.
Keywords: financial data visualization | cryptocurrency market analysis | trading charts | technical analysis tools | market volatility | central bank policies impact | blockchain technology evolution


kai
2025-05-19 18:03
What's shown on the price axis?
What's Shown on the Price Axis? A Guide to Financial Data Visualization and Market Trends
Understanding what is displayed on the price axis is essential for anyone involved in financial markets, whether you're an investor, analyst, or enthusiast. The price axis serves as a visual tool that helps interpret market movements, identify trends, and make informed decisions. This article explores the core elements of the price axis in data visualization, its significance across different markets—including cryptocurrencies—and recent developments shaping how prices are represented.
What Is the Price Axis in Financial Charts?
The price axis is a fundamental component of financial charts that visually represents an asset's value over time. It typically appears as a vertical line or scale alongside horizontal axes representing time intervals. By plotting asset prices—such as stocks, cryptocurrencies, commodities—on this axis, traders and analysts can quickly grasp how values fluctuate within specific periods.
In practical terms, when you look at a candlestick chart for Bitcoin or a line graph for stock prices, the vertical scale indicates how much each asset costs at any given point. This visual cue allows users to detect upward or downward trends swiftly and assess market momentum.
Types of Charts That Use the Price Axis
Different chart types utilize the price axis to convey various aspects of market behavior:
- Line Graphs: These connect closing prices over time with continuous lines to highlight overall trends.
- Candlestick Charts: Offering detailed insights into daily trading activity by displaying open, high, low, and close prices within each period.
- Bar Charts: Similar to candlesticks but with bars representing high-low ranges; often used for volume analysis combined with pricing data.
Each chart type provides unique advantages depending on analytical needs—from simple trend identification to detailed pattern recognition.
The Role of Price Axis in Market Analysis
The primary purpose of displaying asset prices visually is to facilitate market analysis. Investors use these charts to identify patterns such as head-and-shoulders formations or support/resistance levels that signal potential reversals or continuations. Recognizing these patterns helps inform buy/sell decisions and manage risk effectively.
Furthermore, analyzing how prices move relative to technical indicators like moving averages or RSI (Relative Strength Index) enhances decision-making accuracy. For example: if Bitcoin's price crosses above its 50-day moving average on a candlestick chart—a signal often interpreted as bullish—it can prompt investors toward buying opportunities.
Cryptocurrency Markets: Volatility Reflected on the Price Axis
Cryptocurrencies have gained prominence partly because their high volatility makes their price movements highly visible on charts. Digital assets like Bitcoin (BTC) and Ethereum (ETH) experience rapid swings driven by factors such as regulatory news or technological updates.
Recent years have seen dramatic shifts—for instance:
- Bitcoin reaching all-time highs near $65K in 2021
- Sharp declines following regulatory crackdowns or macroeconomic shifts
These fluctuations are vividly captured through changes along the cryptocurrency’s price axis—highlighting both risks and opportunities inherent in digital assets.
How Central Bank Policies Influence Prices Displayed on Charts
Monetary policies enacted by central banks significantly impact financial markets' pricing dynamics:
Interest Rate Changes: When central banks like Federal Reserve raise rates—or cut them—it influences borrowing costs affecting stock valuations and currency strength.
Quantitative Easing (QE): Large-scale asset purchases tend to increase liquidity which can inflate asset prices shown along respective axes.
For example: A series of rate hikes might lead investors away from equities into safer assets like bonds; this shift manifests clearly through declining stock prices plotted against time on charts’ axes.
Technological Innovations Impacting How Prices Are Visualized
Advances in blockchain technology have introduced new assets such as NFTs (non-fungible tokens) and DeFi tokens whose values are tracked similarly via specialized charts featuring their own unique behaviors:
- Rapidly changing NFT valuations
- DeFi token yields fluctuating based on protocol performance
Additionally, sophisticated visualization platforms like TradingView enable overlaying multiple technical indicators onto these axes—such as Bollinger Bands or Fibonacci retracements—to refine analysis further.
Regulatory Environment’s Effect on Asset Pricing Representation
Regulatory developments influence not only actual asset values but also how they are perceived visually:
- Introduction of stablecoins has provided more stability within crypto markets
- Crackdowns may cause sudden drops visible immediately along the chart’s vertical scale
Investors monitor these regulatory signals closely since they directly affect confidence levels reflected through sharp movements along both traditional financial instruments’ axes and emerging digital assets' graphs.
Risks That Can Cause Sudden Changes Along The Price Axis
Market sentiment plays a crucial role; positive news about an investment sector can trigger rapid upward spikes while negative headlines may lead swiftly into declines—all visibly represented through steep slopes or gaps in charts:
- Investor sentiment shifts
- Market manipulation tactics especially prevalent among less regulated crypto exchanges
- Broader economic downturns leading investors toward safer havens
Technological risks such as hacking incidents also contribute unpredictability—causing abrupt drops reflected instantly across relevant graphs’ scales.
Why Understanding What Is Shown On The Price Axis Matters
Grasping what information is conveyed through these visual tools enables better risk management and strategic planning. Whether tracking volatile cryptocurrencies during turbulent times—or assessing traditional stocks amid economic uncertainty—the ability to interpret changes accurately empowers smarter investment choices.
By staying informed about recent trends—including technological innovations influencing data visualization—and understanding external factors like policy shifts—you position yourself advantageously within dynamic markets where every movement along that critical vertical scale counts.
Keywords: financial data visualization | cryptocurrency market analysis | trading charts | technical analysis tools | market volatility | central bank policies impact | blockchain technology evolution
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
How Does Blockchain Technology Work?
Understanding the fundamentals of blockchain technology is essential for grasping its transformative potential across various industries. At its core, blockchain is a decentralized digital ledger that records transactions securely and transparently. Unlike traditional databases managed by central authorities, blockchain distributes data across a network of computers, ensuring no single point of control or failure.
Decentralization is one of the key features that make blockchain unique. Each participant in the network, often called a node, holds an identical copy of the entire ledger. This setup not only enhances security but also promotes transparency because every transaction recorded on the blockchain is visible to all participants. This transparency fosters trust among users and reduces reliance on intermediaries.
The process begins with transaction verification. When someone initiates a transaction—such as transferring cryptocurrency or recording data—the transaction must be validated by nodes within the network. These nodes use consensus mechanisms like proof-of-work (PoW) or proof-of-stake (PoS) to agree on whether the transaction is legitimate before it can be added to the chain.
Once verified, transactions are grouped into blocks. Each block contains multiple transactions along with metadata such as timestamps and cryptographic hashes linking it to previous blocks in the chain—a process known as chaining blocks together cryptographically. This linkage ensures that once a block has been added, altering any information within it would require changing all subsequent blocks—a computationally infeasible task under normal circumstances.
Adding new blocks involves miners or validators performing complex computations (in PoW systems) or staking tokens (in PoS systems). For example, Bitcoin’s proof-of-work requires miners to solve mathematical puzzles; this process consumes significant energy but secures the network against malicious attacks by making tampering costly and resource-intensive.
Cryptography plays an integral role throughout this process—securing data through algorithms such as hashing functions and public-private key encryption. Hash functions generate unique identifiers for each block; any change in data results in a different hash value, alerting participants to potential tampering attempts.
The immutability feature means that once data has been recorded onto a block and added to the chain, it cannot be altered retroactively without detection—this property builds trustworthiness into blockchain applications ranging from financial services to supply chain management.
Blockchain's origins trace back to 2008 when Satoshi Nakamoto published his whitepaper introducing Bitcoin—a peer-to-peer electronic cash system utilizing blockchain technology for secure digital currency transactions without centralized oversight. Since then, innovations have expanded beyond cryptocurrencies into areas like smart contracts—self-executing agreements coded directly onto blockchains—and decentralized finance (DeFi), which offers financial services without traditional intermediaries.
Despite its strengths, understanding how blockchain works also involves recognizing current challenges such as scalability issues where networks struggle with high transaction volumes; environmental concerns due to energy-intensive mining processes; regulatory uncertainties affecting adoption; and security vulnerabilities related mainly to smart contract bugs rather than inherent flaws in underlying protocols.
In summary, blockchain operates through a combination of decentralization, cryptographic security measures, consensus mechanisms for validating transactions—and immutable record-keeping—that collectively create transparent yet secure digital ledgers capable of transforming numerous sectors beyond just cryptocurrencies.


JCUSER-IC8sJL1q
2025-05-14 05:39
How does blockchain technology work?
How Does Blockchain Technology Work?
Understanding the fundamentals of blockchain technology is essential for grasping its transformative potential across various industries. At its core, blockchain is a decentralized digital ledger that records transactions securely and transparently. Unlike traditional databases managed by central authorities, blockchain distributes data across a network of computers, ensuring no single point of control or failure.
Decentralization is one of the key features that make blockchain unique. Each participant in the network, often called a node, holds an identical copy of the entire ledger. This setup not only enhances security but also promotes transparency because every transaction recorded on the blockchain is visible to all participants. This transparency fosters trust among users and reduces reliance on intermediaries.
The process begins with transaction verification. When someone initiates a transaction—such as transferring cryptocurrency or recording data—the transaction must be validated by nodes within the network. These nodes use consensus mechanisms like proof-of-work (PoW) or proof-of-stake (PoS) to agree on whether the transaction is legitimate before it can be added to the chain.
Once verified, transactions are grouped into blocks. Each block contains multiple transactions along with metadata such as timestamps and cryptographic hashes linking it to previous blocks in the chain—a process known as chaining blocks together cryptographically. This linkage ensures that once a block has been added, altering any information within it would require changing all subsequent blocks—a computationally infeasible task under normal circumstances.
Adding new blocks involves miners or validators performing complex computations (in PoW systems) or staking tokens (in PoS systems). For example, Bitcoin’s proof-of-work requires miners to solve mathematical puzzles; this process consumes significant energy but secures the network against malicious attacks by making tampering costly and resource-intensive.
Cryptography plays an integral role throughout this process—securing data through algorithms such as hashing functions and public-private key encryption. Hash functions generate unique identifiers for each block; any change in data results in a different hash value, alerting participants to potential tampering attempts.
The immutability feature means that once data has been recorded onto a block and added to the chain, it cannot be altered retroactively without detection—this property builds trustworthiness into blockchain applications ranging from financial services to supply chain management.
Blockchain's origins trace back to 2008 when Satoshi Nakamoto published his whitepaper introducing Bitcoin—a peer-to-peer electronic cash system utilizing blockchain technology for secure digital currency transactions without centralized oversight. Since then, innovations have expanded beyond cryptocurrencies into areas like smart contracts—self-executing agreements coded directly onto blockchains—and decentralized finance (DeFi), which offers financial services without traditional intermediaries.
Despite its strengths, understanding how blockchain works also involves recognizing current challenges such as scalability issues where networks struggle with high transaction volumes; environmental concerns due to energy-intensive mining processes; regulatory uncertainties affecting adoption; and security vulnerabilities related mainly to smart contract bugs rather than inherent flaws in underlying protocols.
In summary, blockchain operates through a combination of decentralization, cryptographic security measures, consensus mechanisms for validating transactions—and immutable record-keeping—that collectively create transparent yet secure digital ledgers capable of transforming numerous sectors beyond just cryptocurrencies.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
How Do Slippage and Commissions Impact Backtested Trading Results?
Backtesting is a vital process for traders and investors to evaluate the potential performance of trading strategies before deploying real capital. It allows for testing ideas against historical market data, helping traders refine their approaches. However, the accuracy of backtest results can be significantly affected by factors like slippage and commissions—two elements that often get overlooked but are crucial for realistic performance assessment.
Understanding Slippage in Trading
Slippage occurs when there is a difference between the expected price of a trade and the actual execution price. This phenomenon is common in fast-moving or illiquid markets, where prices can change rapidly between order placement and execution. For example, if you place a market order to buy Bitcoin at $30,000, but due to high volatility or low liquidity, your order executes at $30,050 instead—this additional cost is slippage.
In backtesting scenarios, failing to account for slippage can lead to overly optimistic results because it assumes trades are executed exactly at desired prices. In real-world trading environments—especially in cryptocurrency markets known for their volatility—slippage can erode profit margins or turn profitable strategies into losses.
There are two main types of slippage:
- Market Order Slippage: Happens when executing market orders; prices may differ from current quotes.
- Limit Order Slippage: Occurs when limit orders are filled at different prices than specified due to market conditions.
Understanding these distinctions helps traders better model realistic outcomes during backtests.
The Role of Commissions in Trading Performance
Commissions refer to fees charged by exchanges or brokers each time a trade is executed. These fees vary widely depending on the platform—for instance, some exchanges charge flat fees per trade while others use tiered structures based on volume or type (maker vs. taker).
In many backtests, commissions are either simplified or ignored altogether; however, this oversight can lead to inflated profitability estimates. When factoring in commissions:
- Maker Fees: Paid when providing liquidity by placing limit orders that add depth to the order book.
- Taker Fees: Paid when removing liquidity through immediate execution of market orders.
For active traders who execute numerous trades daily—or high-frequency trading algorithms—the cumulative impact of commissions becomes substantial enough to influence overall strategy viability significantly.
How Slippage and Commissions Affect Backtest Accuracy
Ignoring these costs during backtesting creates an overly optimistic picture that might not hold up under live conditions. Specifically:
Overestimating Profits: Without accounting for transaction costs and execution delays caused by slippage, strategies may appear more profitable than they truly are.
Underestimating Risks: Strategies optimized without considering these factors might perform poorly once deployed because actual trading costs eat into profits or exacerbate losses.
Misleading Optimization Results: Overfitting models based solely on idealized data leads traders toward strategies unlikely to succeed outside controlled simulations.
Research indicates that neglecting slippage and commissions can inflate perceived strategy performance by as much as 30%. This discrepancy underscores why incorporating realistic assumptions about transaction costs is essential for credible backtesting outcomes.
Recent Advances in Modeling Slippage & Commissions
The evolving landscape of cryptocurrency markets has prompted researchers and software developers alike to improve how they simulate real-world trading conditions during backtests:
Sophisticated Modeling Techniques: Modern models now incorporate variables such as bid-ask spreads, order book depth analysis, recent volatility measures—and even simulate different types of orders—to produce more accurate estimates.
Enhanced Data Transparency from Exchanges: Many platforms now provide detailed fee structures alongside historical data feeds which help traders estimate commission costs more precisely.
Liquidity Analysis Tools: New tools analyze market liquidity metrics over various timeframes so traders can better understand potential slippages under different conditions—a critical factor given crypto markets' notorious volatility spikes.
These developments enable more reliable simulation environments where risks associated with transaction costs mirror those encountered during live trading sessions closely.
Practical Tips for Incorporating Costs into Backtests
To ensure your backtest results reflect real-world scenarios accurately:
- Use historical bid-ask spreads along with volume data whenever possible.
- Model both maker and taker fee structures relevant to your chosen exchange(s).
- Simulate different levels of slippage based on recent volatility patterns rather than assuming zero-cost executions.
- Regularly update your models with new data reflecting changing market dynamics.
- Leverage advanced software tools like Backtrader or Zipline that support built-in features for modeling transaction costs effectively.
By following these best practices—and understanding how each factor influences outcomes—you'll develop more robust strategies less prone to failure once traded live.
Potential Risks When Ignoring These Factors
Failing to consider slippages and commissions carries notable risks:
Traders may develop overly aggressive expectations about profitability leading them astray once they face actual trading frictions.
Overfitted strategies optimized under idealized assumptions tend not only fail but could also incur significant financial losses if unaccounted-for costs eat away margins unexpectedly.
Misjudging risk-reward ratios due solely on pristine backtest results increases exposure—not just financially but also psychologically—as discrepancies between simulated success and real-world performance shake confidence in one's approach.
Improving Strategy Development Through Realistic Backtesting Conditions
Integrating accurate models of transaction costs enhances strategic robustness considerably—a necessity especially within volatile crypto markets where rapid price swings amplify both opportunities and risks alike.. By acknowledging how slippages occur across different order types (market vs limit) alongside precise commission calculations tailored per exchange’s fee structure enables better risk management decisions before risking actual capital.
Final Thoughts: Building Trustworthy Strategies
Incorporating considerations such as slippages and commissions isn't merely an academic exercise—it’s fundamental for developing trustworthy trading systems capable of performing consistently over time.. As technology advances—with improved modeling techniques—and transparency around exchange fees increases—traders have greater tools available today than ever before.. Embracing these developments ensures your strategy evaluations remain grounded in reality rather than idealized assumptions.
By doing so you reduce surprises during live deployment while increasing confidence that your approach will withstand unpredictable market movements.. Ultimately this leads toward smarter decision-making rooted firmly in comprehensive risk assessment principles essential across all levels—from beginner enthusiasts through seasoned professionals seeking sustainable growth paths within dynamic cryptocurrency landscapes


JCUSER-F1IIaxXA
2025-05-14 05:21
How do slippage and commissions impact backtested results?
How Do Slippage and Commissions Impact Backtested Trading Results?
Backtesting is a vital process for traders and investors to evaluate the potential performance of trading strategies before deploying real capital. It allows for testing ideas against historical market data, helping traders refine their approaches. However, the accuracy of backtest results can be significantly affected by factors like slippage and commissions—two elements that often get overlooked but are crucial for realistic performance assessment.
Understanding Slippage in Trading
Slippage occurs when there is a difference between the expected price of a trade and the actual execution price. This phenomenon is common in fast-moving or illiquid markets, where prices can change rapidly between order placement and execution. For example, if you place a market order to buy Bitcoin at $30,000, but due to high volatility or low liquidity, your order executes at $30,050 instead—this additional cost is slippage.
In backtesting scenarios, failing to account for slippage can lead to overly optimistic results because it assumes trades are executed exactly at desired prices. In real-world trading environments—especially in cryptocurrency markets known for their volatility—slippage can erode profit margins or turn profitable strategies into losses.
There are two main types of slippage:
- Market Order Slippage: Happens when executing market orders; prices may differ from current quotes.
- Limit Order Slippage: Occurs when limit orders are filled at different prices than specified due to market conditions.
Understanding these distinctions helps traders better model realistic outcomes during backtests.
The Role of Commissions in Trading Performance
Commissions refer to fees charged by exchanges or brokers each time a trade is executed. These fees vary widely depending on the platform—for instance, some exchanges charge flat fees per trade while others use tiered structures based on volume or type (maker vs. taker).
In many backtests, commissions are either simplified or ignored altogether; however, this oversight can lead to inflated profitability estimates. When factoring in commissions:
- Maker Fees: Paid when providing liquidity by placing limit orders that add depth to the order book.
- Taker Fees: Paid when removing liquidity through immediate execution of market orders.
For active traders who execute numerous trades daily—or high-frequency trading algorithms—the cumulative impact of commissions becomes substantial enough to influence overall strategy viability significantly.
How Slippage and Commissions Affect Backtest Accuracy
Ignoring these costs during backtesting creates an overly optimistic picture that might not hold up under live conditions. Specifically:
Overestimating Profits: Without accounting for transaction costs and execution delays caused by slippage, strategies may appear more profitable than they truly are.
Underestimating Risks: Strategies optimized without considering these factors might perform poorly once deployed because actual trading costs eat into profits or exacerbate losses.
Misleading Optimization Results: Overfitting models based solely on idealized data leads traders toward strategies unlikely to succeed outside controlled simulations.
Research indicates that neglecting slippage and commissions can inflate perceived strategy performance by as much as 30%. This discrepancy underscores why incorporating realistic assumptions about transaction costs is essential for credible backtesting outcomes.
Recent Advances in Modeling Slippage & Commissions
The evolving landscape of cryptocurrency markets has prompted researchers and software developers alike to improve how they simulate real-world trading conditions during backtests:
Sophisticated Modeling Techniques: Modern models now incorporate variables such as bid-ask spreads, order book depth analysis, recent volatility measures—and even simulate different types of orders—to produce more accurate estimates.
Enhanced Data Transparency from Exchanges: Many platforms now provide detailed fee structures alongside historical data feeds which help traders estimate commission costs more precisely.
Liquidity Analysis Tools: New tools analyze market liquidity metrics over various timeframes so traders can better understand potential slippages under different conditions—a critical factor given crypto markets' notorious volatility spikes.
These developments enable more reliable simulation environments where risks associated with transaction costs mirror those encountered during live trading sessions closely.
Practical Tips for Incorporating Costs into Backtests
To ensure your backtest results reflect real-world scenarios accurately:
- Use historical bid-ask spreads along with volume data whenever possible.
- Model both maker and taker fee structures relevant to your chosen exchange(s).
- Simulate different levels of slippage based on recent volatility patterns rather than assuming zero-cost executions.
- Regularly update your models with new data reflecting changing market dynamics.
- Leverage advanced software tools like Backtrader or Zipline that support built-in features for modeling transaction costs effectively.
By following these best practices—and understanding how each factor influences outcomes—you'll develop more robust strategies less prone to failure once traded live.
Potential Risks When Ignoring These Factors
Failing to consider slippages and commissions carries notable risks:
Traders may develop overly aggressive expectations about profitability leading them astray once they face actual trading frictions.
Overfitted strategies optimized under idealized assumptions tend not only fail but could also incur significant financial losses if unaccounted-for costs eat away margins unexpectedly.
Misjudging risk-reward ratios due solely on pristine backtest results increases exposure—not just financially but also psychologically—as discrepancies between simulated success and real-world performance shake confidence in one's approach.
Improving Strategy Development Through Realistic Backtesting Conditions
Integrating accurate models of transaction costs enhances strategic robustness considerably—a necessity especially within volatile crypto markets where rapid price swings amplify both opportunities and risks alike.. By acknowledging how slippages occur across different order types (market vs limit) alongside precise commission calculations tailored per exchange’s fee structure enables better risk management decisions before risking actual capital.
Final Thoughts: Building Trustworthy Strategies
Incorporating considerations such as slippages and commissions isn't merely an academic exercise—it’s fundamental for developing trustworthy trading systems capable of performing consistently over time.. As technology advances—with improved modeling techniques—and transparency around exchange fees increases—traders have greater tools available today than ever before.. Embracing these developments ensures your strategy evaluations remain grounded in reality rather than idealized assumptions.
By doing so you reduce surprises during live deployment while increasing confidence that your approach will withstand unpredictable market movements.. Ultimately this leads toward smarter decision-making rooted firmly in comprehensive risk assessment principles essential across all levels—from beginner enthusiasts through seasoned professionals seeking sustainable growth paths within dynamic cryptocurrency landscapes
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Psychological Pitfalls of Trading: Understanding the Hidden Risks
Trading in financial markets—whether traditional stocks, forex, or cryptocurrencies—is as much a psychological challenge as it is a financial one. While many traders focus on technical analysis, market trends, and economic indicators, the human mind often introduces biases and emotional reactions that can undermine even the most well-planned strategies. Recognizing these psychological pitfalls is essential for anyone looking to improve their trading performance and safeguard their investments.
Common Psychological Biases That Affect Traders
Human cognition is prone to several biases that can distort decision-making during trading activities. These biases often operate subconsciously but have tangible impacts on trading outcomes.
Confirmation Bias
Confirmation bias occurs when traders seek out information that supports their existing beliefs while ignoring evidence that contradicts them. For example, a trader convinced that a particular stock will rise might only pay attention to positive news and dismiss negative signals. This selective perception can lead to holding onto losing positions longer than advisable or doubling down on flawed assumptions.
Loss Aversion
Loss aversion describes the tendency for individuals to prefer avoiding losses over acquiring equivalent gains. In practical terms, traders may hold onto losing assets in hopes of recovery or hesitate to cut losses early due to fear of realizing a loss. This behavior often results in larger-than-necessary losses and hampers portfolio performance.
Overconfidence
Overconfidence manifests when traders overestimate their abilities or knowledge about market movements. Such overconfidence can lead to excessive risk-taking—like investing large sums without proper analysis—or neglecting risk management tools such as stop-loss orders. When predictions fail, overconfident traders are more likely to suffer significant setbacks.
Herding Behavior
Herding involves following the crowd rather than relying on independent analysis. During periods of market euphoria or panic, many investors buy or sell en masse based solely on collective sentiment rather than fundamentals. This behavior amplifies volatility and can cause bubbles or crashes driven by emotional contagion rather than intrinsic value.
Emotional Trading: Fear and Greed
Emotions play a pivotal role in trading decisions; fear prompts premature selling during downturns while greed encourages chasing after quick profits during peaks. Both extremes lead to impulsive actions—selling at lows or buying at highs—that deviate from rational strategies rooted in analysis.
Cognitive Biases Impacting Trading Decisions
Beyond common biases like confirmation bias and herding behavior, other cognitive distortions influence how traders interpret information:
- Anchoring Bias: Relying heavily on initial data points (such as first impressions about an asset) can skew future expectations.
- Framing Effect: The way information is presented influences decisions; positive framing tends to encourage risk-taking whereas negative framing fosters caution.
- Availability Heuristic: Recent vivid events (like sudden crashes) disproportionately impact judgment about future risks.
- Hindsight Bias: After an event occurs, traders may believe they "knew it all along," leading to unwarranted confidence in predictive abilities.
- Regret Aversion: To avoid feelings of regret from making wrong choices—such as selling too early—traders might cling onto losing positions longer than optimal.
Understanding these biases helps investors develop awareness around subconscious influences affecting their trades.
Recent Trends Amplifying Psychological Challenges
The landscape of trading has evolved rapidly with technological advances and social dynamics adding new layers of complexity:
Cryptocurrency Market Volatility
Cryptocurrencies are notorious for extreme price swings driven by speculative interest rather than fundamental valuation metrics. This volatility intensifies emotional responses like greed during rallies and panic during declines — fueling impulsive trades based more on sentiment than strategy.
Influence of Social Media
Platforms like Twitter Reddit have democratized access but also amplified herd mentality through viral posts and influencer opinions without thorough vetting processes. Rapid dissemination of rumors or hype can trigger swift market moves disconnected from underlying fundamentals—a phenomenon known as "social media-driven herding."
Technological Innovations & AI Tools
While algorithmic trading offers sophisticated insights, reliance solely on automated systems may reinforce existing biases if not used critically by humans overseeing them properly — potentially leading toward overconfidence in machine-generated signals instead of fundamental analysis.
Educational Initiatives & Behavioral Finance Awareness
Growing efforts aim at improving trader education regarding behavioral finance principles help mitigate some psychological pitfalls by fostering better self-awareness among investors about their cognitive tendencies.
Potential Consequences for Traders & Markets
Failing to recognize psychological pitfalls doesn't just affect individual portfolios—it has broader implications:
- Financial Losses: Poor decision-making rooted in bias leads directly to suboptimal trades resulting in monetary setbacks.
- Market Instability: Collective herding behaviors contribute significantly toward bubbles bursting or sudden crashes due purely from mass psychology rather than economic fundamentals.
- Regulatory Scrutiny: As markets become more volatile due partly to behavioral factors—and sometimes manipulative practices—regulators increase oversight which could impose restrictions impacting trader flexibility.4.. Reputation Damage:** Consistent poor decisions influenced by psychological flaws diminish credibility within professional circles; this affects future opportunities with clients/investors.5.. Mental Health Concerns:** Persistent stress stemming from volatile markets combined with financial losses heightens risks related mental health issues such as anxiety disorders or burnout among active traders.
Strategies To Mitigate Psychological Risks
Awareness alone isn't enough; implementing practical measures helps manage these inherent biases:
- Develop disciplined routines including setting predefined entry/exit points using stop-loss orders.
- Maintain realistic expectations aligned with your risk tolerance levels.
- Regularly review past trades objectively without self-blame but focusing instead on learning opportunities.
- Use journaling techniques for tracking emotions alongside trade decisions—to identify patterns linked with specific biases.
- Seek educational resources focused specifically on behavioral finance principles tailored for active investors.
By understanding both personal psychology and external influences shaping markets today—from social media trends through technological advancements—you position yourself better against common pitfalls that threaten long-term success.
Final Thoughts
Navigating the complex world of trading requires more than just technical skills—it demands keen awareness of your own mental state alongside continuous education about behavioral tendencies influencing decision-making processes . Recognizing prevalent cognitive biases like confirmation bias , loss aversion , herding behavior , along with managing emotions such as fear greed , forms part essential foundation towards becoming a resilient investor capable not only surviving but thriving amid market uncertainties . Staying informed about recent developments—from cryptocurrency volatility through social media impacts—and adopting sound strategies ensures you remain adaptive while minimizing detrimental effects caused by subconscious errors inherent within human nature itself


Lo
2025-05-09 16:14
What are the psychological pitfalls of trading?
Psychological Pitfalls of Trading: Understanding the Hidden Risks
Trading in financial markets—whether traditional stocks, forex, or cryptocurrencies—is as much a psychological challenge as it is a financial one. While many traders focus on technical analysis, market trends, and economic indicators, the human mind often introduces biases and emotional reactions that can undermine even the most well-planned strategies. Recognizing these psychological pitfalls is essential for anyone looking to improve their trading performance and safeguard their investments.
Common Psychological Biases That Affect Traders
Human cognition is prone to several biases that can distort decision-making during trading activities. These biases often operate subconsciously but have tangible impacts on trading outcomes.
Confirmation Bias
Confirmation bias occurs when traders seek out information that supports their existing beliefs while ignoring evidence that contradicts them. For example, a trader convinced that a particular stock will rise might only pay attention to positive news and dismiss negative signals. This selective perception can lead to holding onto losing positions longer than advisable or doubling down on flawed assumptions.
Loss Aversion
Loss aversion describes the tendency for individuals to prefer avoiding losses over acquiring equivalent gains. In practical terms, traders may hold onto losing assets in hopes of recovery or hesitate to cut losses early due to fear of realizing a loss. This behavior often results in larger-than-necessary losses and hampers portfolio performance.
Overconfidence
Overconfidence manifests when traders overestimate their abilities or knowledge about market movements. Such overconfidence can lead to excessive risk-taking—like investing large sums without proper analysis—or neglecting risk management tools such as stop-loss orders. When predictions fail, overconfident traders are more likely to suffer significant setbacks.
Herding Behavior
Herding involves following the crowd rather than relying on independent analysis. During periods of market euphoria or panic, many investors buy or sell en masse based solely on collective sentiment rather than fundamentals. This behavior amplifies volatility and can cause bubbles or crashes driven by emotional contagion rather than intrinsic value.
Emotional Trading: Fear and Greed
Emotions play a pivotal role in trading decisions; fear prompts premature selling during downturns while greed encourages chasing after quick profits during peaks. Both extremes lead to impulsive actions—selling at lows or buying at highs—that deviate from rational strategies rooted in analysis.
Cognitive Biases Impacting Trading Decisions
Beyond common biases like confirmation bias and herding behavior, other cognitive distortions influence how traders interpret information:
- Anchoring Bias: Relying heavily on initial data points (such as first impressions about an asset) can skew future expectations.
- Framing Effect: The way information is presented influences decisions; positive framing tends to encourage risk-taking whereas negative framing fosters caution.
- Availability Heuristic: Recent vivid events (like sudden crashes) disproportionately impact judgment about future risks.
- Hindsight Bias: After an event occurs, traders may believe they "knew it all along," leading to unwarranted confidence in predictive abilities.
- Regret Aversion: To avoid feelings of regret from making wrong choices—such as selling too early—traders might cling onto losing positions longer than optimal.
Understanding these biases helps investors develop awareness around subconscious influences affecting their trades.
Recent Trends Amplifying Psychological Challenges
The landscape of trading has evolved rapidly with technological advances and social dynamics adding new layers of complexity:
Cryptocurrency Market Volatility
Cryptocurrencies are notorious for extreme price swings driven by speculative interest rather than fundamental valuation metrics. This volatility intensifies emotional responses like greed during rallies and panic during declines — fueling impulsive trades based more on sentiment than strategy.
Influence of Social Media
Platforms like Twitter Reddit have democratized access but also amplified herd mentality through viral posts and influencer opinions without thorough vetting processes. Rapid dissemination of rumors or hype can trigger swift market moves disconnected from underlying fundamentals—a phenomenon known as "social media-driven herding."
Technological Innovations & AI Tools
While algorithmic trading offers sophisticated insights, reliance solely on automated systems may reinforce existing biases if not used critically by humans overseeing them properly — potentially leading toward overconfidence in machine-generated signals instead of fundamental analysis.
Educational Initiatives & Behavioral Finance Awareness
Growing efforts aim at improving trader education regarding behavioral finance principles help mitigate some psychological pitfalls by fostering better self-awareness among investors about their cognitive tendencies.
Potential Consequences for Traders & Markets
Failing to recognize psychological pitfalls doesn't just affect individual portfolios—it has broader implications:
- Financial Losses: Poor decision-making rooted in bias leads directly to suboptimal trades resulting in monetary setbacks.
- Market Instability: Collective herding behaviors contribute significantly toward bubbles bursting or sudden crashes due purely from mass psychology rather than economic fundamentals.
- Regulatory Scrutiny: As markets become more volatile due partly to behavioral factors—and sometimes manipulative practices—regulators increase oversight which could impose restrictions impacting trader flexibility.4.. Reputation Damage:** Consistent poor decisions influenced by psychological flaws diminish credibility within professional circles; this affects future opportunities with clients/investors.5.. Mental Health Concerns:** Persistent stress stemming from volatile markets combined with financial losses heightens risks related mental health issues such as anxiety disorders or burnout among active traders.
Strategies To Mitigate Psychological Risks
Awareness alone isn't enough; implementing practical measures helps manage these inherent biases:
- Develop disciplined routines including setting predefined entry/exit points using stop-loss orders.
- Maintain realistic expectations aligned with your risk tolerance levels.
- Regularly review past trades objectively without self-blame but focusing instead on learning opportunities.
- Use journaling techniques for tracking emotions alongside trade decisions—to identify patterns linked with specific biases.
- Seek educational resources focused specifically on behavioral finance principles tailored for active investors.
By understanding both personal psychology and external influences shaping markets today—from social media trends through technological advancements—you position yourself better against common pitfalls that threaten long-term success.
Final Thoughts
Navigating the complex world of trading requires more than just technical skills—it demands keen awareness of your own mental state alongside continuous education about behavioral tendencies influencing decision-making processes . Recognizing prevalent cognitive biases like confirmation bias , loss aversion , herding behavior , along with managing emotions such as fear greed , forms part essential foundation towards becoming a resilient investor capable not only surviving but thriving amid market uncertainties . Staying informed about recent developments—from cryptocurrency volatility through social media impacts—and adopting sound strategies ensures you remain adaptive while minimizing detrimental effects caused by subconscious errors inherent within human nature itself
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Can Beginners Participate in the XT Carnival?
The XT Carnival organized by XT.com is a popular event within the cryptocurrency community, designed to foster engagement, education, and community building. For newcomers to the crypto space, questions often arise about whether they can participate in such events without prior experience. The good news is that yes — beginners are encouraged and welcomed to join the XT Carnival. Here’s a detailed overview of how beginners can get involved and what they should expect.
Understanding the Purpose of XT Carnival for Newcomers
The primary goal of the XT Carnival is to educate users about cryptocurrency trading while providing opportunities for engagement through competitions and interactive sessions. Recognizing that many participants may be new to digital assets, XT.com structures its activities to be inclusive for traders at all levels. This means that even if you’re just starting out or still learning basic concepts like blockchain technology or market analysis, you can find value in participating.
Moreover, educational webinars and workshops specifically target beginners by covering fundamental topics such as how trading works on platforms like XT.com, risk management strategies, and understanding market trends. These resources are designed not only for experienced traders but also with newcomers in mind.
How Beginners Can Participate Effectively
For those new to cryptocurrency trading considering participation in an event like the XT Carnival, preparation is key:
- Register Early: Most events require registration through the platform’s official channels. Signing up early ensures access to all activities.
- Attend Educational Sessions: Webinars tailored for beginners provide essential knowledge that helps build confidence before engaging in trading competitions or other interactive activities.
- Start Small: If participating in trading competitions or demo contests offered during the carnival, start with small amounts or virtual funds if available.
- Leverage Resources: Use educational content provided during webinars and workshops—these often include guides on setting up wallets securely or understanding different cryptocurrencies.
By approaching participation with a learning mindset rather than solely focusing on winning prizes initially, beginners can gain valuable insights into crypto markets while enjoying their first experiences.
What Are The Rewards For Beginners?
Participation incentives such as tokens or cash prizes are common during these events; however, most rewards are accessible regardless of skill level. For newcomers:
- Many platforms offer beginner-friendly contests where initial entry requirements are minimal.
- Educational rewards—such as free courses or exclusive content—are often part of event packages aimed at helping novices deepen their understanding.
- Participation itself provides exposure: engaging actively allows learners to familiarize themselves with live market dynamics safely.
It’s important for beginners not only to aim for prizes but also view these opportunities as practical learning experiences that lay foundations for future success.
Risks & Considerations for New Traders
While beginner-friendly participation is encouraged at events like XL Carnival, it’s crucial to understand certain risks:
- Cryptocurrency markets tend toward high volatility; prices can fluctuate significantly within short periods.
- Trading involves financial risk; never invest more than you’re willing—or able—to lose.
XT.com emphasizes security measures such as two-factor authentication (2FA) and secure wallet integrations which help mitigate some risks associated with online transactions but do not eliminate market risks entirely.
Beginners should approach participation cautiously: start small during competitions and avoid rushing into complex trades until they have gained sufficient knowledge from educational resources provided by platforms like XT.com.
How To Prepare As A Beginner Before Joining
Preparation enhances your chances of making meaningful contributions during an event:
- Learn Basic Concepts: Familiarize yourself with fundamental terms (e.g., blockchain technology, wallets), basic chart reading skills (candlestick patterns), and common trading strategies suitable for novices.
- Use Demo Accounts: Many exchanges offer simulated environments where you can practice without risking real funds—check if this feature is available during carnival events.
- Follow Official Announcements: Keep updated via official channels regarding schedules of webinars/workshops tailored toward newbies.
- Engage Actively During Events: Ask questions during live sessions; participate in quizzes or mini-challenges designed specifically around beginner topics.
This proactive approach will help demystify complex concepts over time while allowing you to enjoy participating fully alongside more experienced traders.
Final Thoughts on Beginner Participation
The design philosophy behind events like XL Carnival clearly aims at inclusivity across experience levels—from complete novices just exploring cryptocurrencies to seasoned traders sharpening their skills further. With accessible educational content coupled with low-entry barriers into contests and activities geared toward learning rather than just winning prizes alone—the platform encourages everyone interested in crypto education regardless of prior knowledge level.
Participating actively offers invaluable hands-on experience which complements theoretical understanding gained from webinars/workshops hosted throughout these occasions—and ultimately helps build confidence needed when venturing into real-world crypto investments later down the line.
Key Takeaways
- Beginners are highly encouraged—and welcomed—to join XL Carnival activities organized by XT.com
- Preparation through education improves both safety awareness & overall experience
- Incentives include tokens & educational rewards suitable even for novice participants
- Always consider market volatility & trade responsibly when engaging beyond demo environments


JCUSER-WVMdslBw
2025-06-09 01:56
Can beginners participate in the XT Carnival?
Can Beginners Participate in the XT Carnival?
The XT Carnival organized by XT.com is a popular event within the cryptocurrency community, designed to foster engagement, education, and community building. For newcomers to the crypto space, questions often arise about whether they can participate in such events without prior experience. The good news is that yes — beginners are encouraged and welcomed to join the XT Carnival. Here’s a detailed overview of how beginners can get involved and what they should expect.
Understanding the Purpose of XT Carnival for Newcomers
The primary goal of the XT Carnival is to educate users about cryptocurrency trading while providing opportunities for engagement through competitions and interactive sessions. Recognizing that many participants may be new to digital assets, XT.com structures its activities to be inclusive for traders at all levels. This means that even if you’re just starting out or still learning basic concepts like blockchain technology or market analysis, you can find value in participating.
Moreover, educational webinars and workshops specifically target beginners by covering fundamental topics such as how trading works on platforms like XT.com, risk management strategies, and understanding market trends. These resources are designed not only for experienced traders but also with newcomers in mind.
How Beginners Can Participate Effectively
For those new to cryptocurrency trading considering participation in an event like the XT Carnival, preparation is key:
- Register Early: Most events require registration through the platform’s official channels. Signing up early ensures access to all activities.
- Attend Educational Sessions: Webinars tailored for beginners provide essential knowledge that helps build confidence before engaging in trading competitions or other interactive activities.
- Start Small: If participating in trading competitions or demo contests offered during the carnival, start with small amounts or virtual funds if available.
- Leverage Resources: Use educational content provided during webinars and workshops—these often include guides on setting up wallets securely or understanding different cryptocurrencies.
By approaching participation with a learning mindset rather than solely focusing on winning prizes initially, beginners can gain valuable insights into crypto markets while enjoying their first experiences.
What Are The Rewards For Beginners?
Participation incentives such as tokens or cash prizes are common during these events; however, most rewards are accessible regardless of skill level. For newcomers:
- Many platforms offer beginner-friendly contests where initial entry requirements are minimal.
- Educational rewards—such as free courses or exclusive content—are often part of event packages aimed at helping novices deepen their understanding.
- Participation itself provides exposure: engaging actively allows learners to familiarize themselves with live market dynamics safely.
It’s important for beginners not only to aim for prizes but also view these opportunities as practical learning experiences that lay foundations for future success.
Risks & Considerations for New Traders
While beginner-friendly participation is encouraged at events like XL Carnival, it’s crucial to understand certain risks:
- Cryptocurrency markets tend toward high volatility; prices can fluctuate significantly within short periods.
- Trading involves financial risk; never invest more than you’re willing—or able—to lose.
XT.com emphasizes security measures such as two-factor authentication (2FA) and secure wallet integrations which help mitigate some risks associated with online transactions but do not eliminate market risks entirely.
Beginners should approach participation cautiously: start small during competitions and avoid rushing into complex trades until they have gained sufficient knowledge from educational resources provided by platforms like XT.com.
How To Prepare As A Beginner Before Joining
Preparation enhances your chances of making meaningful contributions during an event:
- Learn Basic Concepts: Familiarize yourself with fundamental terms (e.g., blockchain technology, wallets), basic chart reading skills (candlestick patterns), and common trading strategies suitable for novices.
- Use Demo Accounts: Many exchanges offer simulated environments where you can practice without risking real funds—check if this feature is available during carnival events.
- Follow Official Announcements: Keep updated via official channels regarding schedules of webinars/workshops tailored toward newbies.
- Engage Actively During Events: Ask questions during live sessions; participate in quizzes or mini-challenges designed specifically around beginner topics.
This proactive approach will help demystify complex concepts over time while allowing you to enjoy participating fully alongside more experienced traders.
Final Thoughts on Beginner Participation
The design philosophy behind events like XL Carnival clearly aims at inclusivity across experience levels—from complete novices just exploring cryptocurrencies to seasoned traders sharpening their skills further. With accessible educational content coupled with low-entry barriers into contests and activities geared toward learning rather than just winning prizes alone—the platform encourages everyone interested in crypto education regardless of prior knowledge level.
Participating actively offers invaluable hands-on experience which complements theoretical understanding gained from webinars/workshops hosted throughout these occasions—and ultimately helps build confidence needed when venturing into real-world crypto investments later down the line.
Key Takeaways
- Beginners are highly encouraged—and welcomed—to join XL Carnival activities organized by XT.com
- Preparation through education improves both safety awareness & overall experience
- Incentives include tokens & educational rewards suitable even for novice participants
- Always consider market volatility & trade responsibly when engaging beyond demo environments
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Can I Participate in Multiple Tutorials at the Same Time?
In the fast-paced world of cryptocurrency and investment education, many learners wonder whether it’s possible—and practical—to attend multiple tutorials simultaneously. With a surge in online learning platforms offering diverse courses, understanding how to effectively manage multiple educational sessions is essential for maximizing learning outcomes without risking burnout or information overload.
Understanding the Growing Popularity of Online Crypto and Investment Tutorials
The rise of digital platforms has democratized access to crypto and investment education. Learners can now choose from a vast array of tutorials covering topics like trading strategies, market analysis, blockchain technology, risk management, and more. These resources are often available on-demand or through live sessions such as webinars or interactive classes. The convenience allows individuals to tailor their learning experience according to their schedules and interests.
This proliferation raises an important question: can one realistically participate in several tutorials at once? The answer depends on various factors including personal discipline, technical setup, content overlap, and the specific structure of each course.
Benefits of Participating in Multiple Tutorials
Engaging with multiple tutorials offers several advantages:
- Comprehensive Learning: Accessing different perspectives helps deepen understanding across various topics within crypto investing.
- Personalized Education: Learners can select courses that match their skill levels—beginners might focus on foundational concepts while advanced traders explore niche strategies.
- Flexibility: Hybrid models combining live sessions with recorded content enable learners to customize their schedules.
- Networking Opportunities: Participating in diverse communities fosters peer support and knowledge sharing.
When managed properly, juggling multiple tutorials can accelerate your mastery over complex subjects like technical analysis or decentralized finance (DeFi).
Challenges Associated with Simultaneous Tutorial Participation
Despite these benefits, there are notable challenges:
Time Management Is Critical
Balancing several courses requires disciplined scheduling. Without effective time management tools—such as calendars or task lists—learners risk missing key lessons or feeling overwhelmed by overlapping commitments.
Content Overlap Risks
Many tutorials cover similar themes; for example, two courses might teach basic chart patterns. While this reinforcement is beneficial if approached thoughtfully, excessive repetition combined with rapid switching between sessions may lead to confusion rather than clarity.
Technical Requirements
Participating actively across multiple platforms demands reliable internet connections and compatible devices (computers or smartphones). Technical glitches like lagging streams or login issues can disrupt your learning flow when attending concurrent sessions.
Cognitive Load & Burnout
Trying to absorb too much information simultaneously may cause mental fatigue. Overexertion could lead learners toward burnout—a state characterized by exhaustion and decreased motivation—which ultimately hampers progress.
Recent Developments Supporting Multi-Tutorial Engagement
Innovations within online education have made participating in multiple tutorials more feasible:
Hybrid Learning Models: Combining asynchronous (self-paced) content with live interactions provides flexibility that accommodates busy schedules.
Artificial Intelligence Tools: AI-powered scheduling assistants suggest optimal times for attending different classes based on individual preferences and workload capacity.
Specialized Courses & Niche Topics: The growth of niche educational offerings allows learners to focus deeply on specific areas without spreading themselves too thin across unrelated subjects.
Community Platforms: Forums integrated into tutorial platforms foster peer-to-peer support where participants share insights from different courses—enhancing overall comprehension without needing simultaneous attendance at all sessions.
Potential Pitfalls When Engaging With Multiple Tutorials
While multi-tutorial participation offers advantages, it also presents risks that should be carefully managed:
Information Overload
Trying to keep up with numerous sources may overwhelm your cognitive capacity leading to confusion rather than clarity. It’s crucial not just to consume content but also process it meaningfully before moving onto new material.
Technical Difficulties
Connectivity issues remain a common obstacle; poor internet speed can result in missed lessons or incomplete participation which diminishes learning effectiveness over time.
Burnout & Fatigue
Excessive engagement without adequate breaks increases stress levels; maintaining balance is vital for sustained progress especially when juggling complex topics like derivatives trading alongside blockchain fundamentals.
Quality Control Concerns
Not all online tutorials maintain high standards; selecting reputable providers ensures you receive accurate information aligned with current industry practices while avoiding misinformation pitfalls prevalent among less credible sources.
Scalability Challenges for Platforms
As demand grows for simultaneous multi-course participation, platform infrastructure must scale accordingly; otherwise users might face performance issues such as slow loading times during peak periods.
Tips for Effectively Managing Multiple Crypto & Investment Tutorials
To maximize benefits while minimizing drawbacks:
Use digital calendars (Google Calendar etc.) to schedule tutorial times clearly.
Prioritize quality over quantity by selecting reputable providers known for accurate content delivery.
Limit overlapping live sessions when possible; record webinars if available so you can review them later at your convenience.
Break study periods into manageable chunks—e.g., 30-minute focused blocks—to prevent fatigue.
Engage actively during lessons through note-taking and participating in discussion forums instead of passive viewing.
Real-Life Examples Demonstrating Successful Multi-Tutorial Participation
Many successful investors attribute part of their growth trajectory to engaging with diverse educational resources simultaneously:
Example: Jane Doe started her crypto journey by taking foundational courses on blockchain technology while concurrently attending advanced trading strategy webinars offered by different providers—all scheduled thoughtfully around her work hours using AI-based scheduling tools she adopted early on.*
Her disciplined approach allowed her not only comprehensive knowledge acquisition but also practical application through simulated trading exercises shared within community forums associated with each course platform.
How To Choose High-quality Platforms Supporting Multiple Tutorials
Selecting the right educational platform is critical:
- Look for platforms offering flexible access options—including recorded videos—and integrated discussion communities
- Check reviews regarding course accuracy and instructor credibility
- Ensure compatibility across devices
- Confirm availability of personalized features such as tailored learning paths
- Evaluate customer support responsiveness
By choosing reputable sources that facilitate seamless multi-tutorial engagement — supported by robust technical infrastructure — learners set themselves up for success.
Participating in multiple crypto and investment tutorials simultaneously is entirely feasible when approached strategically—with proper planning around time management , quality selection , technological readiness ,and awareness about potential pitfalls . Embracing recent innovations like hybrid models and AI tools further enhances this approach's practicality . Ultimately , balancing breadth versus depth remains key — enabling motivated individuals not only learn faster but also develop nuanced understanding necessary for navigating today’s dynamic financial landscape effectively


JCUSER-F1IIaxXA
2025-06-05 06:09
Can I participate in multiple tutorials at the same time?
Can I Participate in Multiple Tutorials at the Same Time?
In the fast-paced world of cryptocurrency and investment education, many learners wonder whether it’s possible—and practical—to attend multiple tutorials simultaneously. With a surge in online learning platforms offering diverse courses, understanding how to effectively manage multiple educational sessions is essential for maximizing learning outcomes without risking burnout or information overload.
Understanding the Growing Popularity of Online Crypto and Investment Tutorials
The rise of digital platforms has democratized access to crypto and investment education. Learners can now choose from a vast array of tutorials covering topics like trading strategies, market analysis, blockchain technology, risk management, and more. These resources are often available on-demand or through live sessions such as webinars or interactive classes. The convenience allows individuals to tailor their learning experience according to their schedules and interests.
This proliferation raises an important question: can one realistically participate in several tutorials at once? The answer depends on various factors including personal discipline, technical setup, content overlap, and the specific structure of each course.
Benefits of Participating in Multiple Tutorials
Engaging with multiple tutorials offers several advantages:
- Comprehensive Learning: Accessing different perspectives helps deepen understanding across various topics within crypto investing.
- Personalized Education: Learners can select courses that match their skill levels—beginners might focus on foundational concepts while advanced traders explore niche strategies.
- Flexibility: Hybrid models combining live sessions with recorded content enable learners to customize their schedules.
- Networking Opportunities: Participating in diverse communities fosters peer support and knowledge sharing.
When managed properly, juggling multiple tutorials can accelerate your mastery over complex subjects like technical analysis or decentralized finance (DeFi).
Challenges Associated with Simultaneous Tutorial Participation
Despite these benefits, there are notable challenges:
Time Management Is Critical
Balancing several courses requires disciplined scheduling. Without effective time management tools—such as calendars or task lists—learners risk missing key lessons or feeling overwhelmed by overlapping commitments.
Content Overlap Risks
Many tutorials cover similar themes; for example, two courses might teach basic chart patterns. While this reinforcement is beneficial if approached thoughtfully, excessive repetition combined with rapid switching between sessions may lead to confusion rather than clarity.
Technical Requirements
Participating actively across multiple platforms demands reliable internet connections and compatible devices (computers or smartphones). Technical glitches like lagging streams or login issues can disrupt your learning flow when attending concurrent sessions.
Cognitive Load & Burnout
Trying to absorb too much information simultaneously may cause mental fatigue. Overexertion could lead learners toward burnout—a state characterized by exhaustion and decreased motivation—which ultimately hampers progress.
Recent Developments Supporting Multi-Tutorial Engagement
Innovations within online education have made participating in multiple tutorials more feasible:
Hybrid Learning Models: Combining asynchronous (self-paced) content with live interactions provides flexibility that accommodates busy schedules.
Artificial Intelligence Tools: AI-powered scheduling assistants suggest optimal times for attending different classes based on individual preferences and workload capacity.
Specialized Courses & Niche Topics: The growth of niche educational offerings allows learners to focus deeply on specific areas without spreading themselves too thin across unrelated subjects.
Community Platforms: Forums integrated into tutorial platforms foster peer-to-peer support where participants share insights from different courses—enhancing overall comprehension without needing simultaneous attendance at all sessions.
Potential Pitfalls When Engaging With Multiple Tutorials
While multi-tutorial participation offers advantages, it also presents risks that should be carefully managed:
Information Overload
Trying to keep up with numerous sources may overwhelm your cognitive capacity leading to confusion rather than clarity. It’s crucial not just to consume content but also process it meaningfully before moving onto new material.
Technical Difficulties
Connectivity issues remain a common obstacle; poor internet speed can result in missed lessons or incomplete participation which diminishes learning effectiveness over time.
Burnout & Fatigue
Excessive engagement without adequate breaks increases stress levels; maintaining balance is vital for sustained progress especially when juggling complex topics like derivatives trading alongside blockchain fundamentals.
Quality Control Concerns
Not all online tutorials maintain high standards; selecting reputable providers ensures you receive accurate information aligned with current industry practices while avoiding misinformation pitfalls prevalent among less credible sources.
Scalability Challenges for Platforms
As demand grows for simultaneous multi-course participation, platform infrastructure must scale accordingly; otherwise users might face performance issues such as slow loading times during peak periods.
Tips for Effectively Managing Multiple Crypto & Investment Tutorials
To maximize benefits while minimizing drawbacks:
Use digital calendars (Google Calendar etc.) to schedule tutorial times clearly.
Prioritize quality over quantity by selecting reputable providers known for accurate content delivery.
Limit overlapping live sessions when possible; record webinars if available so you can review them later at your convenience.
Break study periods into manageable chunks—e.g., 30-minute focused blocks—to prevent fatigue.
Engage actively during lessons through note-taking and participating in discussion forums instead of passive viewing.
Real-Life Examples Demonstrating Successful Multi-Tutorial Participation
Many successful investors attribute part of their growth trajectory to engaging with diverse educational resources simultaneously:
Example: Jane Doe started her crypto journey by taking foundational courses on blockchain technology while concurrently attending advanced trading strategy webinars offered by different providers—all scheduled thoughtfully around her work hours using AI-based scheduling tools she adopted early on.*
Her disciplined approach allowed her not only comprehensive knowledge acquisition but also practical application through simulated trading exercises shared within community forums associated with each course platform.
How To Choose High-quality Platforms Supporting Multiple Tutorials
Selecting the right educational platform is critical:
- Look for platforms offering flexible access options—including recorded videos—and integrated discussion communities
- Check reviews regarding course accuracy and instructor credibility
- Ensure compatibility across devices
- Confirm availability of personalized features such as tailored learning paths
- Evaluate customer support responsiveness
By choosing reputable sources that facilitate seamless multi-tutorial engagement — supported by robust technical infrastructure — learners set themselves up for success.
Participating in multiple crypto and investment tutorials simultaneously is entirely feasible when approached strategically—with proper planning around time management , quality selection , technological readiness ,and awareness about potential pitfalls . Embracing recent innovations like hybrid models and AI tools further enhances this approach's practicality . Ultimately , balancing breadth versus depth remains key — enabling motivated individuals not only learn faster but also develop nuanced understanding necessary for navigating today’s dynamic financial landscape effectively
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Can I Customize My Watchlist on Investing.com?
Investing.com is a widely used platform among traders and investors for accessing real-time financial data, news, and analysis. One of its most valuable features is the ability to create and customize watchlists, which help users monitor specific assets efficiently. If you're wondering whether you can tailor your watchlist to suit your investment strategy, the answer is a definitive yes. This article provides a detailed overview of how customization works on Investing.com, what benefits it offers, and recent updates that enhance user experience.
How Does Watchlist Customization Work on Investing.com?
Investing.com's watchlist feature allows users to organize their preferred stocks, cryptocurrencies, commodities, indices, and other financial instruments into personalized lists. Creating multiple watchlists enables investors to categorize assets based on different criteria such as asset class (stocks vs cryptocurrencies), market regions (US markets vs Asian markets), or investment goals (long-term holdings vs short-term trades). The process involves simple steps: users can add assets directly from search results or market pages by clicking an "Add to Watchlist" button. Once added, these assets appear in the user's customized list for quick access.
The platform supports dynamic editing—users can easily add new assets or remove existing ones depending on changing market conditions or evolving investment strategies. This flexibility ensures that investors stay organized without being overwhelmed by irrelevant data.
Real-Time Data Updates & Alerts
One of the key advantages of customizing a watchlist on Investing.com is receiving real-time updates about selected assets. Market prices fluctuate constantly; therefore, timely information is crucial for making informed decisions. The platform refreshes data automatically so that users see current prices alongside relevant news headlines and technical indicators.
Moreover, investing.com allows setting up alerts tied to specific events such as price thresholds or news releases related to individual assets within your watchlists. These notifications can be delivered via email or push alerts through mobile devices—keeping you informed even when you're away from the platform.
Integration with Trading Platforms
For active traders who prefer executing orders directly from their research environment, investing.com's watchlists are integrated with its trading platforms where available. This seamless connection means you can initiate buy or sell orders without switching apps once you've identified opportunities within your customized lists—a significant efficiency boost for day traders and portfolio managers alike.
Recent Enhancements in Watchlist Features
Over recent years, investing.com has introduced several improvements aimed at enhancing user experience with their watchlists:
- Advanced Visualization Tools: Users now benefit from better graphical representations like heat maps and trend charts embedded within their lists.
- Enhanced Alert Systems: More customizable alert parameters allow precise monitoring—for example: setting alerts only during certain times of day.
- User Feedback Integration: The platform actively incorporates suggestions from its community—resulting in more intuitive interfaces and additional functionalities.
- Broader Integration Capabilities: Efforts have been made toward connecting watchlists with third-party services such as portfolio management tools for comprehensive investment oversight.
Potential Challenges & Security Considerations
While customizing your watchlist offers numerous benefits—such as tailored tracking and improved decision-making—it also comes with some considerations:
During periods of high market volatility (e.g., economic crises), reliance solely on static lists may lead investors astray if they do not adjust their watches accordingly.
Technical issues like server downtime could temporarily prevent access to updated data; thus maintaining backup strategies remains important.
As with any online financial service handling sensitive information—including personalized asset preferences—security measures are vital. Investing.com employs encryption protocols; however security breaches remain a risk if user accounts are not protected adequately through strong passwords and two-factor authentication options.
Why Customizing Your Watchlist Matters for Investors
Personalized monitoring tools like custom watchlists empower both novice investors seeking structured guidance and experienced traders aiming for rapid response capabilities. By organizing relevant instruments into manageable groups—and receiving timely updates—they reduce cognitive overload while increasing situational awareness in fast-moving markets.
Furthermore, integrating these lists into trading workflows streamlines decision-making processes: you identify opportunities quickly without sifting through unrelated data streams repeatedly. As markets evolve rapidly today—with new cryptocurrencies emerging daily or geopolitical events impacting commodity prices—the ability to adapt your monitoring setup becomes essential for maintaining an edge.
Final Thoughts
Yes—you absolutely can customize your watchlist on Investing.com according to your preferences and needs. The platform's flexible features enable creating multiple lists tailored by asset type or strategy while providing real-time updates coupled with alert systems designed to keep you informed at all times. Recent enhancements continue improving usability—from better visualization options to deeper integrations—all aimed at supporting smarter investment decisions.
By leveraging these capabilities responsibly—and ensuring robust security practices—you maximize the value derived from investing.com's powerful tools while minimizing potential risks associated with online trading environments.
Keywords: customize investing.com watchlist | personalized stock tracker | real-time market alerts | asset management tools | trading platform integration


JCUSER-IC8sJL1q
2025-05-27 07:28
Can I customize my watchlist on Investing.com?
Can I Customize My Watchlist on Investing.com?
Investing.com is a widely used platform among traders and investors for accessing real-time financial data, news, and analysis. One of its most valuable features is the ability to create and customize watchlists, which help users monitor specific assets efficiently. If you're wondering whether you can tailor your watchlist to suit your investment strategy, the answer is a definitive yes. This article provides a detailed overview of how customization works on Investing.com, what benefits it offers, and recent updates that enhance user experience.
How Does Watchlist Customization Work on Investing.com?
Investing.com's watchlist feature allows users to organize their preferred stocks, cryptocurrencies, commodities, indices, and other financial instruments into personalized lists. Creating multiple watchlists enables investors to categorize assets based on different criteria such as asset class (stocks vs cryptocurrencies), market regions (US markets vs Asian markets), or investment goals (long-term holdings vs short-term trades). The process involves simple steps: users can add assets directly from search results or market pages by clicking an "Add to Watchlist" button. Once added, these assets appear in the user's customized list for quick access.
The platform supports dynamic editing—users can easily add new assets or remove existing ones depending on changing market conditions or evolving investment strategies. This flexibility ensures that investors stay organized without being overwhelmed by irrelevant data.
Real-Time Data Updates & Alerts
One of the key advantages of customizing a watchlist on Investing.com is receiving real-time updates about selected assets. Market prices fluctuate constantly; therefore, timely information is crucial for making informed decisions. The platform refreshes data automatically so that users see current prices alongside relevant news headlines and technical indicators.
Moreover, investing.com allows setting up alerts tied to specific events such as price thresholds or news releases related to individual assets within your watchlists. These notifications can be delivered via email or push alerts through mobile devices—keeping you informed even when you're away from the platform.
Integration with Trading Platforms
For active traders who prefer executing orders directly from their research environment, investing.com's watchlists are integrated with its trading platforms where available. This seamless connection means you can initiate buy or sell orders without switching apps once you've identified opportunities within your customized lists—a significant efficiency boost for day traders and portfolio managers alike.
Recent Enhancements in Watchlist Features
Over recent years, investing.com has introduced several improvements aimed at enhancing user experience with their watchlists:
- Advanced Visualization Tools: Users now benefit from better graphical representations like heat maps and trend charts embedded within their lists.
- Enhanced Alert Systems: More customizable alert parameters allow precise monitoring—for example: setting alerts only during certain times of day.
- User Feedback Integration: The platform actively incorporates suggestions from its community—resulting in more intuitive interfaces and additional functionalities.
- Broader Integration Capabilities: Efforts have been made toward connecting watchlists with third-party services such as portfolio management tools for comprehensive investment oversight.
Potential Challenges & Security Considerations
While customizing your watchlist offers numerous benefits—such as tailored tracking and improved decision-making—it also comes with some considerations:
During periods of high market volatility (e.g., economic crises), reliance solely on static lists may lead investors astray if they do not adjust their watches accordingly.
Technical issues like server downtime could temporarily prevent access to updated data; thus maintaining backup strategies remains important.
As with any online financial service handling sensitive information—including personalized asset preferences—security measures are vital. Investing.com employs encryption protocols; however security breaches remain a risk if user accounts are not protected adequately through strong passwords and two-factor authentication options.
Why Customizing Your Watchlist Matters for Investors
Personalized monitoring tools like custom watchlists empower both novice investors seeking structured guidance and experienced traders aiming for rapid response capabilities. By organizing relevant instruments into manageable groups—and receiving timely updates—they reduce cognitive overload while increasing situational awareness in fast-moving markets.
Furthermore, integrating these lists into trading workflows streamlines decision-making processes: you identify opportunities quickly without sifting through unrelated data streams repeatedly. As markets evolve rapidly today—with new cryptocurrencies emerging daily or geopolitical events impacting commodity prices—the ability to adapt your monitoring setup becomes essential for maintaining an edge.
Final Thoughts
Yes—you absolutely can customize your watchlist on Investing.com according to your preferences and needs. The platform's flexible features enable creating multiple lists tailored by asset type or strategy while providing real-time updates coupled with alert systems designed to keep you informed at all times. Recent enhancements continue improving usability—from better visualization options to deeper integrations—all aimed at supporting smarter investment decisions.
By leveraging these capabilities responsibly—and ensuring robust security practices—you maximize the value derived from investing.com's powerful tools while minimizing potential risks associated with online trading environments.
Keywords: customize investing.com watchlist | personalized stock tracker | real-time market alerts | asset management tools | trading platform integration
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
What Is an Options Greeks Chart?
An options Greeks chart is a visual tool that displays the sensitivities of an options contract to various market factors. It helps traders understand how different variables—such as time, volatility, and underlying asset price movements—impact the value of their options. By providing a clear graphical representation, these charts enable more informed decision-making in options trading.
Options trading involves contracts that give buyers the right—but not the obligation—to buy or sell an underlying asset at a predetermined price (strike price) before a specific date (expiration). The risks associated with these trades are complex, but they can be quantified using what are known as "the Greeks." These metrics measure how sensitive an option’s price is to changes in key market variables.
Key Components of Options Greeks
Understanding the core components of an options Greeks chart begins with familiarizing yourself with five primary metrics: Delta, Gamma, Theta, Vega, and Rho. Each plays a vital role in assessing risk and potential profit.
Delta
Delta measures how much an option's price will change for each $1 move in the underlying asset’s price. For call options (which give the right to buy), delta ranges from 0 to 1; for put options (which give the right to sell), it ranges from -1 to 0. A delta close to 1 or -1 indicates high sensitivity—meaning small changes in stock prices can significantly impact option value.
Gamma
Gamma indicates how much delta will change when the underlying asset's price shifts by $1. It essentially measures the curvature or convexity of your position’s payoff profile. Gamma tends to be highest for at-the-money options and diminishes as you move further into or out of money. High gamma implies greater sensitivity but also increased risk if markets move unexpectedly.
Theta
Theta reflects time decay—the rate at which an option loses value as expiration approaches if all other factors remain constant. This metric is crucial because it underscores that holding long positions in options involves facing ongoing erosion of value over time—a phenomenon traders must consider when planning entry and exit strategies.
Vega
Vega measures how much an option's premium will change given a 1% increase or decrease in implied volatility—the market’s forecasted fluctuation level for underlying assets. Higher vega values are typical for longer-term or at-the-money options where volatility has more influence on pricing dynamics.
Rho
Rho assesses sensitivity relative to interest rate changes; specifically, it shows how much an option's value would shift with a one percentage point change in interest rates. While generally less impactful than other Greeks under normal conditions, rho becomes more significant during periods of rapid economic shifts or monetary policy adjustments.
How Options Greeks Are Visualized on Charts
Options Greeks charts typically display multiple curves representing each Greek across different scenarios—for example, varying stock prices or times until expiration. These visualizations help traders quickly grasp complex relationships:
- Delta curves illustrate potential directional moves.
- Gamma surfaces highlight areas where small movements could lead to large swings.
- Theta heatmaps show decay rates over time.
- Vega contours reveal regions sensitive to volatility shifts.
By integrating these elements into one comprehensive chart, traders gain insights into their exposure levels under various market conditions—enhancing risk management strategies effectively.
Recent Trends Enhancing Usefulness
The adoption and sophistication of Options Greeks charts have grown significantly over recent years due mainly to technological advancements and expanding markets like cryptocurrencies:
Crypto Market Integration: As digital assets gained popularity since around 2020, traders began applying traditional derivatives concepts—including Greek analysis—to manage crypto derivatives' unique risks amid high volatility.
Enhanced Trading Platforms: Modern platforms now offer interactive tools allowing real-time visualization of Greek sensitivities alongside live data feeds—making complex analysis accessible even for less experienced traders.
Educational Resources: The surge in online courses—from webinars through blogs—has democratized understanding about interpreting Greek charts correctly while emphasizing their limitations when used alone without broader analysis frameworks.
Financial institutions also incorporate advanced Greek analytics into their proprietary tools for deeper market insights—a trend likely driven by increasing demand from institutional investors seeking sophisticated risk assessment methods.
Risks Associated With Overreliance on Option Greeks
While Options Greeks provide valuable information about potential risks and rewards within your portfolio—they should not be viewed as infallible predictors:
Overemphasizing any single metric can lead traders astray; combining multiple indicators along with fundamental analysis yields better results.
In volatile environments like crypto markets—or during sudden economic shocks—the significance of Vega and Gamma increases sharply but so does unpredictability; large swings may cause substantial losses if not properly hedged.
Time decay (Theta) emphasizes timing importance: holding onto positions too long without adjusting can erode gains rapidly near expiration dates.
Furthermore, although Rho generally exerts minimal influence compared with other metrics under normal circumstances—it may become relevant during periods marked by rapid interest rate fluctuations caused by macroeconomic policies such as inflation control measures or monetary easing programs.
Using Options Greeks Effectively
To leverage this powerful analytical framework successfully:
Combine Greek data with technical analysis patterns such as support/resistance levelsand volume trends for comprehensive insight.
Regularly monitor changes across all relevant metrics rather than relying solely on static snapshots—they evolve dynamically based on market conditions
Use scenario analyses provided by Greek charts—for example,simulating sharp increases/decreases in implied volatility—to prepare contingency plans
This integrated approach enhances your ability both defensively hedge against adverse movesand proactively capitalize on favorable trends.
The Evolution & Future Outlook
Since their inception back in the 1970s—with continuous refinements through financial modeling advances—the use cases surrounding Options Greeks have expanded considerably:
Their application has moved beyond traditional equities markets into burgeoning sectors like cryptocurrency derivatives since around 2020
Trading platforms now routinely embed sophisticated visualization tools enabling real-time monitoring
Educational content continues proliferating online—from beginner guides through advanced workshops—that emphasizes responsible use alongside cautionary notes about limitations
Looking ahead,the integration between artificial intelligence-driven analyticsand real-time data streams promises even deeper insights,potentially transforming how retail investors manage risk using these critical metrics.
By understanding what constitutes an Options Greeks chart—and recognizing its strengths alongside its limitations—you empower yourself better equipped for navigating today's complex financial landscapes whether trading stocks or digital assets alike. Remember: effective risk management combines quantitative insights like those provided by Greece calculations with sound judgment rooted in thorough research—and always considers broader macroeconomic contexts influencing markets globally.


kai
2025-05-20 05:16
What’s an Options Greeks chart?
What Is an Options Greeks Chart?
An options Greeks chart is a visual tool that displays the sensitivities of an options contract to various market factors. It helps traders understand how different variables—such as time, volatility, and underlying asset price movements—impact the value of their options. By providing a clear graphical representation, these charts enable more informed decision-making in options trading.
Options trading involves contracts that give buyers the right—but not the obligation—to buy or sell an underlying asset at a predetermined price (strike price) before a specific date (expiration). The risks associated with these trades are complex, but they can be quantified using what are known as "the Greeks." These metrics measure how sensitive an option’s price is to changes in key market variables.
Key Components of Options Greeks
Understanding the core components of an options Greeks chart begins with familiarizing yourself with five primary metrics: Delta, Gamma, Theta, Vega, and Rho. Each plays a vital role in assessing risk and potential profit.
Delta
Delta measures how much an option's price will change for each $1 move in the underlying asset’s price. For call options (which give the right to buy), delta ranges from 0 to 1; for put options (which give the right to sell), it ranges from -1 to 0. A delta close to 1 or -1 indicates high sensitivity—meaning small changes in stock prices can significantly impact option value.
Gamma
Gamma indicates how much delta will change when the underlying asset's price shifts by $1. It essentially measures the curvature or convexity of your position’s payoff profile. Gamma tends to be highest for at-the-money options and diminishes as you move further into or out of money. High gamma implies greater sensitivity but also increased risk if markets move unexpectedly.
Theta
Theta reflects time decay—the rate at which an option loses value as expiration approaches if all other factors remain constant. This metric is crucial because it underscores that holding long positions in options involves facing ongoing erosion of value over time—a phenomenon traders must consider when planning entry and exit strategies.
Vega
Vega measures how much an option's premium will change given a 1% increase or decrease in implied volatility—the market’s forecasted fluctuation level for underlying assets. Higher vega values are typical for longer-term or at-the-money options where volatility has more influence on pricing dynamics.
Rho
Rho assesses sensitivity relative to interest rate changes; specifically, it shows how much an option's value would shift with a one percentage point change in interest rates. While generally less impactful than other Greeks under normal conditions, rho becomes more significant during periods of rapid economic shifts or monetary policy adjustments.
How Options Greeks Are Visualized on Charts
Options Greeks charts typically display multiple curves representing each Greek across different scenarios—for example, varying stock prices or times until expiration. These visualizations help traders quickly grasp complex relationships:
- Delta curves illustrate potential directional moves.
- Gamma surfaces highlight areas where small movements could lead to large swings.
- Theta heatmaps show decay rates over time.
- Vega contours reveal regions sensitive to volatility shifts.
By integrating these elements into one comprehensive chart, traders gain insights into their exposure levels under various market conditions—enhancing risk management strategies effectively.
Recent Trends Enhancing Usefulness
The adoption and sophistication of Options Greeks charts have grown significantly over recent years due mainly to technological advancements and expanding markets like cryptocurrencies:
Crypto Market Integration: As digital assets gained popularity since around 2020, traders began applying traditional derivatives concepts—including Greek analysis—to manage crypto derivatives' unique risks amid high volatility.
Enhanced Trading Platforms: Modern platforms now offer interactive tools allowing real-time visualization of Greek sensitivities alongside live data feeds—making complex analysis accessible even for less experienced traders.
Educational Resources: The surge in online courses—from webinars through blogs—has democratized understanding about interpreting Greek charts correctly while emphasizing their limitations when used alone without broader analysis frameworks.
Financial institutions also incorporate advanced Greek analytics into their proprietary tools for deeper market insights—a trend likely driven by increasing demand from institutional investors seeking sophisticated risk assessment methods.
Risks Associated With Overreliance on Option Greeks
While Options Greeks provide valuable information about potential risks and rewards within your portfolio—they should not be viewed as infallible predictors:
Overemphasizing any single metric can lead traders astray; combining multiple indicators along with fundamental analysis yields better results.
In volatile environments like crypto markets—or during sudden economic shocks—the significance of Vega and Gamma increases sharply but so does unpredictability; large swings may cause substantial losses if not properly hedged.
Time decay (Theta) emphasizes timing importance: holding onto positions too long without adjusting can erode gains rapidly near expiration dates.
Furthermore, although Rho generally exerts minimal influence compared with other metrics under normal circumstances—it may become relevant during periods marked by rapid interest rate fluctuations caused by macroeconomic policies such as inflation control measures or monetary easing programs.
Using Options Greeks Effectively
To leverage this powerful analytical framework successfully:
Combine Greek data with technical analysis patterns such as support/resistance levelsand volume trends for comprehensive insight.
Regularly monitor changes across all relevant metrics rather than relying solely on static snapshots—they evolve dynamically based on market conditions
Use scenario analyses provided by Greek charts—for example,simulating sharp increases/decreases in implied volatility—to prepare contingency plans
This integrated approach enhances your ability both defensively hedge against adverse movesand proactively capitalize on favorable trends.
The Evolution & Future Outlook
Since their inception back in the 1970s—with continuous refinements through financial modeling advances—the use cases surrounding Options Greeks have expanded considerably:
Their application has moved beyond traditional equities markets into burgeoning sectors like cryptocurrency derivatives since around 2020
Trading platforms now routinely embed sophisticated visualization tools enabling real-time monitoring
Educational content continues proliferating online—from beginner guides through advanced workshops—that emphasizes responsible use alongside cautionary notes about limitations
Looking ahead,the integration between artificial intelligence-driven analyticsand real-time data streams promises even deeper insights,potentially transforming how retail investors manage risk using these critical metrics.
By understanding what constitutes an Options Greeks chart—and recognizing its strengths alongside its limitations—you empower yourself better equipped for navigating today's complex financial landscapes whether trading stocks or digital assets alike. Remember: effective risk management combines quantitative insights like those provided by Greece calculations with sound judgment rooted in thorough research—and always considers broader macroeconomic contexts influencing markets globally.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
How Range-Bound Strategies Can Effectively Use Oscillators in Cryptocurrency Trading
Understanding Range-Bound Trading in Crypto Markets
Range-bound trading is a popular strategy among cryptocurrency traders, especially during periods when the market lacks a clear directional trend. In this approach, traders identify specific support and resistance levels—price points where the asset tends to bounce back or face rejection—and execute trades within this confined range. The goal is to profit from predictable oscillations rather than attempting to predict breakouts or sustained trends.
Cryptocurrencies are known for their high volatility, which can make trend-following strategies risky during sideways markets. Therefore, range-bound strategies offer an alternative by focusing on price stability within defined boundaries. This method requires precise analysis tools that can signal potential entry and exit points without relying solely on price action.
What Are Oscillators and Why Are They Important?
Oscillators are technical indicators designed to measure momentum and market sentiment by analyzing recent price movements. Unlike trend-following tools such as moving averages, oscillators fluctuate between predefined levels—typically overbought and oversold zones—making them particularly useful for identifying potential reversals within a range.
Some of the most common oscillators used in crypto trading include:
- Relative Strength Index (RSI): Measures the speed and change of recent price movements to identify overbought (>70) or oversold (<30) conditions.
- Stochastic Oscillator: Compares closing prices with their trading ranges over a specified period, signaling potential reversals when crossing certain thresholds.
- Moving Average Convergence Divergence (MACD): Tracks momentum shifts through moving average crossovers, confirming trend strength or weakness.
These tools help traders interpret whether an asset is likely to reverse direction soon—a critical insight when operating within a confined range.
Leveraging Oscillators for Range-Bound Trading
Using oscillators effectively enhances the precision of range-bound strategies by providing timely signals about market conditions. Here’s how traders can leverage these tools:
1. Detect Overbought and Oversold Conditions
When an oscillator indicates that an asset is overbought near resistance levels or oversold near support zones, it suggests that a reversal might be imminent. For example:
- An RSI reading above 70 at resistance could signal that buying pressure has peaked.
- Conversely, RSI below 30 at support might indicate selling exhaustion.
These signals enable traders to enter short positions near resistance or long positions near support with higher confidence.
2. Anticipate Price Reversals
Oscillators don’t just confirm current conditions—they also help anticipate upcoming reversals before they fully materialize in price charts. For instance:
- A stochastic oscillator crossing above its oversold threshold may precede upward movement.
- MACD crossovers can confirm weakening momentum before prices turn around.
By monitoring these signals closely within the established range boundaries, traders can optimize entry points while minimizing risk exposure.
3. Confirm Market Sentiment & Trend Strength
While ranges imply sideways movement, understanding whether there’s underlying strength behind these moves is crucial for decision-making:
- Divergences between oscillator readings and price action often hint at weakening momentum—potentially signaling an impending breakout.
For example:
- If prices remain flat but RSI shows divergence (lower lows while prices stay stable), it could suggest exhaustion of selling pressure.
This helps differentiate false signals from genuine opportunities within the range.
4. Improve Risk Management Strategies
Oscillators assist in setting more effective stop-loss orders by indicating when assets are nearing extreme conditions:
- Placing stops slightly beyond identified support/resistance levels when oscillators show overextended readings reduces unnecessary losses if reversal signals fail.
In volatile crypto markets where sudden swings are common, combining oscillator insights with other analysis methods enhances overall risk control measures.
Recent Trends Enhancing Range-Bound Strategies with Oscillators
The integration of artificial intelligence into technical analysis has marked significant progress recently. AI-driven oscillators adapt dynamically to changing market environments by learning from historical data patterns—a step beyond traditional static indicators like RSI or MACD alone.
Moreover, increased community engagement on social media platforms highlights growing interest among retail investors leveraging these tools effectively during sideways markets — especially amid heightened crypto volatility post-pandemic era developments like DeFi growth and institutional participation increases.
Another notable development involves combining multiple oscillators—for instance using RSI alongside Stochastic—to generate more reliable trade signals through consensus confirmation rather than relying on single indicator outputs alone.
Risks & Limitations When Using Oscillators in Range Trading
Despite their advantages, reliance solely on oscillatory indicators carries risks that every trader should consider:
Overdependence: Relying exclusively on one indicator may lead to false positives; integrating other forms of analysis such as volume studies or fundamental insights improves decision accuracy.*
Market Conditions: External factors like liquidity constraints or macroeconomic news events can distort oscillator readings’ reliability.*
Regulatory Impact: Changes in cryptocurrency regulations might influence market behavior unpredictably—rendering some technical setups less effective temporarily.*
Therefore, successful application demands comprehensive analysis combining multiple data sources along with sound risk management practices.
Final Thoughts: Combining Tools for Better Outcomes
Range-bound strategies paired with well-understood oscillator use form a robust framework for navigating sideways crypto markets efficiently. By recognizing key signs such as overbought/oversold states and divergences early through these indicators—and supplementing them with AI advancements—traders gain valuable edge against unpredictable volatility inherent in digital assets today.
Staying informed about ongoing technological innovations while maintaining disciplined risk controls will continue shaping how effectively traders leverage oscillatory tools inside confined ranges — ultimately leading toward smarter decision-making amid complex market dynamics.


Lo
2025-05-14 02:52
How can range-bound strategies leverage oscillators effectively?
How Range-Bound Strategies Can Effectively Use Oscillators in Cryptocurrency Trading
Understanding Range-Bound Trading in Crypto Markets
Range-bound trading is a popular strategy among cryptocurrency traders, especially during periods when the market lacks a clear directional trend. In this approach, traders identify specific support and resistance levels—price points where the asset tends to bounce back or face rejection—and execute trades within this confined range. The goal is to profit from predictable oscillations rather than attempting to predict breakouts or sustained trends.
Cryptocurrencies are known for their high volatility, which can make trend-following strategies risky during sideways markets. Therefore, range-bound strategies offer an alternative by focusing on price stability within defined boundaries. This method requires precise analysis tools that can signal potential entry and exit points without relying solely on price action.
What Are Oscillators and Why Are They Important?
Oscillators are technical indicators designed to measure momentum and market sentiment by analyzing recent price movements. Unlike trend-following tools such as moving averages, oscillators fluctuate between predefined levels—typically overbought and oversold zones—making them particularly useful for identifying potential reversals within a range.
Some of the most common oscillators used in crypto trading include:
- Relative Strength Index (RSI): Measures the speed and change of recent price movements to identify overbought (>70) or oversold (<30) conditions.
- Stochastic Oscillator: Compares closing prices with their trading ranges over a specified period, signaling potential reversals when crossing certain thresholds.
- Moving Average Convergence Divergence (MACD): Tracks momentum shifts through moving average crossovers, confirming trend strength or weakness.
These tools help traders interpret whether an asset is likely to reverse direction soon—a critical insight when operating within a confined range.
Leveraging Oscillators for Range-Bound Trading
Using oscillators effectively enhances the precision of range-bound strategies by providing timely signals about market conditions. Here’s how traders can leverage these tools:
1. Detect Overbought and Oversold Conditions
When an oscillator indicates that an asset is overbought near resistance levels or oversold near support zones, it suggests that a reversal might be imminent. For example:
- An RSI reading above 70 at resistance could signal that buying pressure has peaked.
- Conversely, RSI below 30 at support might indicate selling exhaustion.
These signals enable traders to enter short positions near resistance or long positions near support with higher confidence.
2. Anticipate Price Reversals
Oscillators don’t just confirm current conditions—they also help anticipate upcoming reversals before they fully materialize in price charts. For instance:
- A stochastic oscillator crossing above its oversold threshold may precede upward movement.
- MACD crossovers can confirm weakening momentum before prices turn around.
By monitoring these signals closely within the established range boundaries, traders can optimize entry points while minimizing risk exposure.
3. Confirm Market Sentiment & Trend Strength
While ranges imply sideways movement, understanding whether there’s underlying strength behind these moves is crucial for decision-making:
- Divergences between oscillator readings and price action often hint at weakening momentum—potentially signaling an impending breakout.
For example:
- If prices remain flat but RSI shows divergence (lower lows while prices stay stable), it could suggest exhaustion of selling pressure.
This helps differentiate false signals from genuine opportunities within the range.
4. Improve Risk Management Strategies
Oscillators assist in setting more effective stop-loss orders by indicating when assets are nearing extreme conditions:
- Placing stops slightly beyond identified support/resistance levels when oscillators show overextended readings reduces unnecessary losses if reversal signals fail.
In volatile crypto markets where sudden swings are common, combining oscillator insights with other analysis methods enhances overall risk control measures.
Recent Trends Enhancing Range-Bound Strategies with Oscillators
The integration of artificial intelligence into technical analysis has marked significant progress recently. AI-driven oscillators adapt dynamically to changing market environments by learning from historical data patterns—a step beyond traditional static indicators like RSI or MACD alone.
Moreover, increased community engagement on social media platforms highlights growing interest among retail investors leveraging these tools effectively during sideways markets — especially amid heightened crypto volatility post-pandemic era developments like DeFi growth and institutional participation increases.
Another notable development involves combining multiple oscillators—for instance using RSI alongside Stochastic—to generate more reliable trade signals through consensus confirmation rather than relying on single indicator outputs alone.
Risks & Limitations When Using Oscillators in Range Trading
Despite their advantages, reliance solely on oscillatory indicators carries risks that every trader should consider:
Overdependence: Relying exclusively on one indicator may lead to false positives; integrating other forms of analysis such as volume studies or fundamental insights improves decision accuracy.*
Market Conditions: External factors like liquidity constraints or macroeconomic news events can distort oscillator readings’ reliability.*
Regulatory Impact: Changes in cryptocurrency regulations might influence market behavior unpredictably—rendering some technical setups less effective temporarily.*
Therefore, successful application demands comprehensive analysis combining multiple data sources along with sound risk management practices.
Final Thoughts: Combining Tools for Better Outcomes
Range-bound strategies paired with well-understood oscillator use form a robust framework for navigating sideways crypto markets efficiently. By recognizing key signs such as overbought/oversold states and divergences early through these indicators—and supplementing them with AI advancements—traders gain valuable edge against unpredictable volatility inherent in digital assets today.
Staying informed about ongoing technological innovations while maintaining disciplined risk controls will continue shaping how effectively traders leverage oscillatory tools inside confined ranges — ultimately leading toward smarter decision-making amid complex market dynamics.
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
How Can You Avoid Phishing Attacks?
Phishing remains one of the most prevalent and dangerous cyber threats facing individuals and organizations today. As attackers develop more sophisticated tactics, understanding how to protect yourself from falling victim is essential. This article provides practical strategies rooted in recent cybersecurity developments to help you recognize, prevent, and respond to phishing attempts effectively.
Understanding Phishing and Its Risks
Phishing involves deceptive communications—most commonly emails—that appear legitimate but are designed to trick recipients into revealing sensitive information such as passwords, credit card details, or personal data. Attackers often exploit human psychology by creating a sense of urgency or trustworthiness, making it easier for them to manipulate victims.
Recent trends show that phishing attacks are becoming increasingly targeted (spear phishing) or personalized (whaling), especially aimed at high-level executives or specific departments within organizations. The rise of AI-powered phishing tools further complicates defense efforts by enabling highly convincing fake messages that can bypass traditional security filters.
The consequences of falling for a phishing scam can be severe: financial losses, data breaches leading to identity theft, damage to reputation—particularly for businesses—and potential legal liabilities. Therefore, proactive measures are vital in safeguarding your digital assets.
Recognize Common Signs of Phishing Attempts
Being able to identify suspicious messages is the first line of defense. Typical signs include:
- Unexpected requests for confidential information
- Urgent language demanding immediate action ("Your account will be suspended")
- Unusual sender email addresses that mimic legitimate ones
- Spelling mistakes or grammatical errors
- Suspicious links that do not match official URLs
- Attachments from unknown sources
In recent developments like Google's AI-enhanced Chrome security features using Gemini Nano technology, users receive smarter alerts about potentially malicious sites or links before clicking them. Staying alert and cautious when encountering these signs significantly reduces risk exposure.
Implement Strong Authentication Measures
One effective way to prevent unauthorized access resulting from phishing is adopting multi-factor authentication (MFA). Even if attackers manage to steal login credentials through a successful phishing attempt, MFA adds an extra layer—such as a one-time code sent via SMS or generated by an authenticator app—that makes unauthorized access much harder.
Microsoft's recent initiative with passkeys exemplifies this approach by replacing shared secrets with cryptographic keys stored securely on devices. Passkeys eliminate many vulnerabilities associated with traditional passwords and make credential theft via phishing considerably less feasible.
Organizations should encourage employees and users alike to enable MFA across all critical accounts—including email services, banking platforms, cloud storage solutions—and ensure they understand how it works.
Be Cautious With Links and Attachments
Links embedded within emails can easily redirect you toward malicious websites designed explicitly for harvesting login details or installing malware on your device. Hovering over links without clicking reveals their true destination URL; if it looks suspicious or mismatched with the sender's domain—especially in spear-phishing campaigns—it’s best not to click.
Similarly, avoid opening attachments unless you're expecting them from trusted sources. Cybercriminals often use attachments containing malware payloads disguised as invoices or documents relevant to the recipient's work role.
Regularly updating your software—including browsers and antivirus programs—is crucial because many recent threats exploit known vulnerabilities that updates patch effectively. For example: Google's enhanced security measures leverage AI algorithms trained on vast datasets of malicious activity patterns; keeping software current ensures compatibility with these protections.
Educate Yourself About Latest Threats
Staying informed about evolving cyberattack techniques enhances your ability to recognize potential threats early on. Recent reports indicate an increase in credential theft attacks surpassing traditional ransomware incidents—a trend driven partly by sophisticated social engineering tactics enabled through AI tools like ChatGPT-generated messages tailored specifically for targets' interests.
Organizations should conduct regular cybersecurity awareness training sessions covering topics such as recognizing fake websites (pharming), avoiding sharing sensitive info over unsecured channels like SMS (smishing), and reporting suspicious activity promptly through designated channels.
Government agencies and cybersecurity firms frequently publish updates about emerging scams; subscribing ensures you remain aware of new attack vectors targeting both individuals and enterprises alike.
Practical Steps To Protect Yourself From Phishing Attacks:
Use Strong Passwords & Enable Multi-Factor Authentication
Create complex passwords combining letters, numbers,and symbols; activate MFA wherever possible.Verify Sender Details Carefully
Always double-check email addresses against official contacts before responding.
3.. Avoid Clicking Unverified Links
Hover over links first; do not click if anything seems off.
4.. Keep Software Up-to-Date
Regularly install updates for operating systems,browsers,and security tools.
5.. Be Wary Of Urgent Requests
Attackers often create false sense of urgency—think twice before acting immediately.
6.. Educate Yourself & Others
Stay informed about current scams through reputable cybersecurity news sources.
The Role Of Technology In Preventing Phishing Attacks
Advancements such as AI-powered defenses introduced recently by companies like Google enhance detection capabilities against sophisticated scams[2]. These systems analyze patterns across millions of interactions in real time — flagging potentially malicious content before reaching users’ inboxes—or warning them during browsing sessions[3].
Furthermore,the adoption of passkeys represents a significant shift away from vulnerable password-based authentication towards more secure methods resistantto social engineering[3]. Combining technological solutions with user education creates a layered defense system capableof mitigating even advanced threats effectively.
Final Thoughts: Staying Vigilant Against Phishing Threats
While technological innovations continue improving our defenses against cyberattacks like phishing,[1][2][3], human vigilance remains paramount.[4] Recognizing warning signs,promoting good security habits,and staying updated on emerging tactics form the foundationof effective protection strategies.[5]
By integrating strong authentication practices,safe browsing behaviors,and ongoing education,you significantly reduce your chancesof falling victimto these pervasive scams.[1][2] Remember: Cybersecurity is an ongoing process—not just a one-time effort—and staying vigilant is keyto maintaining digital safety in today’s interconnected world.[4][5]


JCUSER-F1IIaxXA
2025-05-11 11:52
How can you avoid phishing attacks?
How Can You Avoid Phishing Attacks?
Phishing remains one of the most prevalent and dangerous cyber threats facing individuals and organizations today. As attackers develop more sophisticated tactics, understanding how to protect yourself from falling victim is essential. This article provides practical strategies rooted in recent cybersecurity developments to help you recognize, prevent, and respond to phishing attempts effectively.
Understanding Phishing and Its Risks
Phishing involves deceptive communications—most commonly emails—that appear legitimate but are designed to trick recipients into revealing sensitive information such as passwords, credit card details, or personal data. Attackers often exploit human psychology by creating a sense of urgency or trustworthiness, making it easier for them to manipulate victims.
Recent trends show that phishing attacks are becoming increasingly targeted (spear phishing) or personalized (whaling), especially aimed at high-level executives or specific departments within organizations. The rise of AI-powered phishing tools further complicates defense efforts by enabling highly convincing fake messages that can bypass traditional security filters.
The consequences of falling for a phishing scam can be severe: financial losses, data breaches leading to identity theft, damage to reputation—particularly for businesses—and potential legal liabilities. Therefore, proactive measures are vital in safeguarding your digital assets.
Recognize Common Signs of Phishing Attempts
Being able to identify suspicious messages is the first line of defense. Typical signs include:
- Unexpected requests for confidential information
- Urgent language demanding immediate action ("Your account will be suspended")
- Unusual sender email addresses that mimic legitimate ones
- Spelling mistakes or grammatical errors
- Suspicious links that do not match official URLs
- Attachments from unknown sources
In recent developments like Google's AI-enhanced Chrome security features using Gemini Nano technology, users receive smarter alerts about potentially malicious sites or links before clicking them. Staying alert and cautious when encountering these signs significantly reduces risk exposure.
Implement Strong Authentication Measures
One effective way to prevent unauthorized access resulting from phishing is adopting multi-factor authentication (MFA). Even if attackers manage to steal login credentials through a successful phishing attempt, MFA adds an extra layer—such as a one-time code sent via SMS or generated by an authenticator app—that makes unauthorized access much harder.
Microsoft's recent initiative with passkeys exemplifies this approach by replacing shared secrets with cryptographic keys stored securely on devices. Passkeys eliminate many vulnerabilities associated with traditional passwords and make credential theft via phishing considerably less feasible.
Organizations should encourage employees and users alike to enable MFA across all critical accounts—including email services, banking platforms, cloud storage solutions—and ensure they understand how it works.
Be Cautious With Links and Attachments
Links embedded within emails can easily redirect you toward malicious websites designed explicitly for harvesting login details or installing malware on your device. Hovering over links without clicking reveals their true destination URL; if it looks suspicious or mismatched with the sender's domain—especially in spear-phishing campaigns—it’s best not to click.
Similarly, avoid opening attachments unless you're expecting them from trusted sources. Cybercriminals often use attachments containing malware payloads disguised as invoices or documents relevant to the recipient's work role.
Regularly updating your software—including browsers and antivirus programs—is crucial because many recent threats exploit known vulnerabilities that updates patch effectively. For example: Google's enhanced security measures leverage AI algorithms trained on vast datasets of malicious activity patterns; keeping software current ensures compatibility with these protections.
Educate Yourself About Latest Threats
Staying informed about evolving cyberattack techniques enhances your ability to recognize potential threats early on. Recent reports indicate an increase in credential theft attacks surpassing traditional ransomware incidents—a trend driven partly by sophisticated social engineering tactics enabled through AI tools like ChatGPT-generated messages tailored specifically for targets' interests.
Organizations should conduct regular cybersecurity awareness training sessions covering topics such as recognizing fake websites (pharming), avoiding sharing sensitive info over unsecured channels like SMS (smishing), and reporting suspicious activity promptly through designated channels.
Government agencies and cybersecurity firms frequently publish updates about emerging scams; subscribing ensures you remain aware of new attack vectors targeting both individuals and enterprises alike.
Practical Steps To Protect Yourself From Phishing Attacks:
Use Strong Passwords & Enable Multi-Factor Authentication
Create complex passwords combining letters, numbers,and symbols; activate MFA wherever possible.Verify Sender Details Carefully
Always double-check email addresses against official contacts before responding.
3.. Avoid Clicking Unverified Links
Hover over links first; do not click if anything seems off.
4.. Keep Software Up-to-Date
Regularly install updates for operating systems,browsers,and security tools.
5.. Be Wary Of Urgent Requests
Attackers often create false sense of urgency—think twice before acting immediately.
6.. Educate Yourself & Others
Stay informed about current scams through reputable cybersecurity news sources.
The Role Of Technology In Preventing Phishing Attacks
Advancements such as AI-powered defenses introduced recently by companies like Google enhance detection capabilities against sophisticated scams[2]. These systems analyze patterns across millions of interactions in real time — flagging potentially malicious content before reaching users’ inboxes—or warning them during browsing sessions[3].
Furthermore,the adoption of passkeys represents a significant shift away from vulnerable password-based authentication towards more secure methods resistantto social engineering[3]. Combining technological solutions with user education creates a layered defense system capableof mitigating even advanced threats effectively.
Final Thoughts: Staying Vigilant Against Phishing Threats
While technological innovations continue improving our defenses against cyberattacks like phishing,[1][2][3], human vigilance remains paramount.[4] Recognizing warning signs,promoting good security habits,and staying updated on emerging tactics form the foundationof effective protection strategies.[5]
By integrating strong authentication practices,safe browsing behaviors,and ongoing education,you significantly reduce your chancesof falling victimto these pervasive scams.[1][2] Remember: Cybersecurity is an ongoing process—not just a one-time effort—and staying vigilant is keyto maintaining digital safety in today’s interconnected world.[4][5]
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
How Do Footprint Charts Enhance Order Flow Trading Strategies?
Understanding Footprint Charts and Their Role in Trading
Footprint charts, also known as order flow charts, have become an essential component of modern trading analysis. Unlike traditional price charts that focus solely on price movements over time, footprint charts provide a granular view of market activity by visualizing every executed buy and sell order. Each vertical line on the chart represents a specific time interval, with its position indicating the price level and its color or shading revealing whether buyers or sellers dominated during that period.
This detailed visualization allows traders to see real-time order flow dynamics—such as where liquidity is concentrated, how imbalances between buy and sell orders develop, and potential areas where market sentiment might shift. By offering this depth of insight, footprint charts enable traders to move beyond basic technical indicators and engage in more precise decision-making based on actual market participation.
How Footprint Charts Improve Order Flow Analysis
Order flow trading hinges on understanding the intentions behind executed trades. Traditional tools like volume bars or candlestick patterns provide some information but often lack the immediacy or detail needed for high-precision strategies. Footprint charts bridge this gap by displaying:
- Order Imbalances: Highlighting whether buying or selling pressure is stronger at specific levels.
- Liquidity Zones: Identifying areas with high concentrations of orders that can act as support or resistance.
- Market Sentiment: Gauging overall trader behavior through the distribution of buy versus sell orders over time.
These features help traders detect early signs of trend reversals or continuations before they become apparent through conventional analysis methods. For example, a sudden increase in aggressive buying at a support level may signal an impending upward move—information that can be immediately observed via footprint data.
Enhancing Trading Strategies with Footprint Charts
Integrating footprint charts into existing trading frameworks significantly enhances strategic robustness. Traders often combine them with technical analysis tools such as moving averages, Fibonacci retracements, or momentum indicators to validate signals derived from order flow data.
Some practical ways footprint charts improve strategies include:
- Timing Entries and Exits: Spotting moments when buy/sell imbalances suggest strong directional moves.
- Managing Risk: Recognizing liquidity gaps helps avoid slippage during trade execution.
- Confirming Breakouts: Validating breakouts through increased order activity rather than relying solely on price action.
By providing real-time insights into how market participants are acting at specific levels, these charts allow for more confident decision-making rooted in actual market behavior rather than assumptions alone.
Recent Trends: Adoption Across Markets
Initially popular among professional futures traders and institutional investors due to their complexity and costliness, footprint charts are now gaining traction across various markets—including cryptocurrencies. The rise of digital assets has accelerated demand because crypto markets operate 24/7 with high volatility—making detailed order flow analysis particularly valuable.
Furthermore, advancements in analytics software have made it easier for retail traders to access these tools without extensive technical expertise. Many platforms now offer integrated footprint chart features alongside traditional charting options—empowering individual traders to incorporate sophisticated order flow insights into their routines seamlessly.
Limitations: Market Manipulation Risks & Regulatory Concerns
Despite their advantages, footprint charts are not without drawbacks. Their transparency can sometimes be exploited by malicious actors seeking to manipulate markets through techniques like spoofing (placing fake orders) which distort perceived supply/demand levels visible on these diagrams.
Additionally, regulatory bodies worldwide are increasingly scrutinizing advanced trading tools like footprints due to concerns about fairness and transparency—especially within unregulated crypto exchanges where such data could give certain players an unfair advantage if misused.
As adoption grows rapidly across different asset classes—from equities to commodities—the industry must balance innovation with oversight measures designed to prevent abuse while maintaining fair access for all participants.
How To Use Footprint Charts Effectively In Your Trading Strategy
To maximize benefits from footprint chart analysis within your trading approach:
- Combine them with other technical indicators for confirmation.
- Focus on identifying persistent imbalances rather than short-term anomalies.
- Pay attention to liquidity zones; they often mark significant turning points.
- Use real-time data feeds for timely decision-making during volatile periods.
Future Outlook: Evolving Technologies & Market Impact
The evolution of technology continues shaping how traders utilize footprints in their strategies:
- Advanced analytics powered by artificial intelligence (AI) enhance pattern recognition capabilities.
- Machine learning models interpret complex footprints faster than manual methods.
- Increased regulation may lead toward standardized usage protocols ensuring fair play across platforms.
Final Thoughts: The Significance Of Footprint Charts In Modern Trading
Footprint charts have transformed how professional traders analyze market activity by providing unparalleled visibility into buyer-seller interactions at each moment in time—a crucial edge especially amid volatile environments like cryptocurrency markets today. When integrated thoughtfully within comprehensive trading plans—and used responsibly considering potential manipulation risks—they serve as powerful tools enabling more informed decisions rooted directly in actual market participation patterns.
Keywords: foot print chart benefits | order flow strategy | analyzing buy-sell imbalance | liquidity zones | advanced analytics in trading | crypto market insights | trade timing using footprints


JCUSER-WVMdslBw
2025-05-09 21:19
How do footprint charts enhance order flow trading strategies?
How Do Footprint Charts Enhance Order Flow Trading Strategies?
Understanding Footprint Charts and Their Role in Trading
Footprint charts, also known as order flow charts, have become an essential component of modern trading analysis. Unlike traditional price charts that focus solely on price movements over time, footprint charts provide a granular view of market activity by visualizing every executed buy and sell order. Each vertical line on the chart represents a specific time interval, with its position indicating the price level and its color or shading revealing whether buyers or sellers dominated during that period.
This detailed visualization allows traders to see real-time order flow dynamics—such as where liquidity is concentrated, how imbalances between buy and sell orders develop, and potential areas where market sentiment might shift. By offering this depth of insight, footprint charts enable traders to move beyond basic technical indicators and engage in more precise decision-making based on actual market participation.
How Footprint Charts Improve Order Flow Analysis
Order flow trading hinges on understanding the intentions behind executed trades. Traditional tools like volume bars or candlestick patterns provide some information but often lack the immediacy or detail needed for high-precision strategies. Footprint charts bridge this gap by displaying:
- Order Imbalances: Highlighting whether buying or selling pressure is stronger at specific levels.
- Liquidity Zones: Identifying areas with high concentrations of orders that can act as support or resistance.
- Market Sentiment: Gauging overall trader behavior through the distribution of buy versus sell orders over time.
These features help traders detect early signs of trend reversals or continuations before they become apparent through conventional analysis methods. For example, a sudden increase in aggressive buying at a support level may signal an impending upward move—information that can be immediately observed via footprint data.
Enhancing Trading Strategies with Footprint Charts
Integrating footprint charts into existing trading frameworks significantly enhances strategic robustness. Traders often combine them with technical analysis tools such as moving averages, Fibonacci retracements, or momentum indicators to validate signals derived from order flow data.
Some practical ways footprint charts improve strategies include:
- Timing Entries and Exits: Spotting moments when buy/sell imbalances suggest strong directional moves.
- Managing Risk: Recognizing liquidity gaps helps avoid slippage during trade execution.
- Confirming Breakouts: Validating breakouts through increased order activity rather than relying solely on price action.
By providing real-time insights into how market participants are acting at specific levels, these charts allow for more confident decision-making rooted in actual market behavior rather than assumptions alone.
Recent Trends: Adoption Across Markets
Initially popular among professional futures traders and institutional investors due to their complexity and costliness, footprint charts are now gaining traction across various markets—including cryptocurrencies. The rise of digital assets has accelerated demand because crypto markets operate 24/7 with high volatility—making detailed order flow analysis particularly valuable.
Furthermore, advancements in analytics software have made it easier for retail traders to access these tools without extensive technical expertise. Many platforms now offer integrated footprint chart features alongside traditional charting options—empowering individual traders to incorporate sophisticated order flow insights into their routines seamlessly.
Limitations: Market Manipulation Risks & Regulatory Concerns
Despite their advantages, footprint charts are not without drawbacks. Their transparency can sometimes be exploited by malicious actors seeking to manipulate markets through techniques like spoofing (placing fake orders) which distort perceived supply/demand levels visible on these diagrams.
Additionally, regulatory bodies worldwide are increasingly scrutinizing advanced trading tools like footprints due to concerns about fairness and transparency—especially within unregulated crypto exchanges where such data could give certain players an unfair advantage if misused.
As adoption grows rapidly across different asset classes—from equities to commodities—the industry must balance innovation with oversight measures designed to prevent abuse while maintaining fair access for all participants.
How To Use Footprint Charts Effectively In Your Trading Strategy
To maximize benefits from footprint chart analysis within your trading approach:
- Combine them with other technical indicators for confirmation.
- Focus on identifying persistent imbalances rather than short-term anomalies.
- Pay attention to liquidity zones; they often mark significant turning points.
- Use real-time data feeds for timely decision-making during volatile periods.
Future Outlook: Evolving Technologies & Market Impact
The evolution of technology continues shaping how traders utilize footprints in their strategies:
- Advanced analytics powered by artificial intelligence (AI) enhance pattern recognition capabilities.
- Machine learning models interpret complex footprints faster than manual methods.
- Increased regulation may lead toward standardized usage protocols ensuring fair play across platforms.
Final Thoughts: The Significance Of Footprint Charts In Modern Trading
Footprint charts have transformed how professional traders analyze market activity by providing unparalleled visibility into buyer-seller interactions at each moment in time—a crucial edge especially amid volatile environments like cryptocurrency markets today. When integrated thoughtfully within comprehensive trading plans—and used responsibly considering potential manipulation risks—they serve as powerful tools enabling more informed decisions rooted directly in actual market participation patterns.
Keywords: foot print chart benefits | order flow strategy | analyzing buy-sell imbalance | liquidity zones | advanced analytics in trading | crypto market insights | trade timing using footprints
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
Consumer Protection Risks on Centralized Cryptocurrency Exchanges
Cryptocurrency trading has become increasingly mainstream, with centralized exchanges (CEXs) serving as the primary gateways for millions of users worldwide. While these platforms offer convenience, liquidity, and a wide range of services, they also pose significant consumer protection risks that users should be aware of. Understanding these risks is essential for anyone involved in crypto trading to make informed decisions and safeguard their assets.
What Are Centralized Cryptocurrency Exchanges?
Centralized exchanges are digital platforms that facilitate the buying, selling, and trading of cryptocurrencies by acting as intermediaries between traders. They manage order books, hold user funds in custodial wallets, and often provide additional features such as margin trading or staking options. Popular examples include Binance, Coinbase, Kraken, and Bitfinex.
Unlike decentralized exchanges (DEXs), which operate without a central authority and allow peer-to-peer transactions directly on blockchain networks, CEXs rely on their own infrastructure to execute trades. This centralization simplifies user experience but introduces specific risks related to security and regulatory oversight.
Key Consumer Protection Risks Associated with CEXs
Security Vulnerabilities
One of the most prominent concerns surrounding centralized exchanges is their vulnerability to cyberattacks. High-profile hacks have resulted in massive losses for users; notably, Mt. Gox's 2014 breach led to over 850,000 Bitcoins stolen—an amount worth billions today. These incidents expose how hackers target CEXs due to their large pools of assets stored centrally.
In addition to external threats like hacking attempts or data breaches exposing sensitive information such as personal details or account credentials—insider threats also pose a risk. Employees with access privileges might misuse their authority for personal gain or inadvertently compromise platform security if proper controls are not in place.
Regulatory Compliance Challenges
The regulatory landscape for cryptocurrencies remains complex and inconsistent across jurisdictions. Many countries lack clear frameworks governing CEX operations; some have outright bans while others impose stringent licensing requirements.
This ambiguity can leave consumers unprotected when disputes arise or when platforms fail to adhere strictly to financial regulations like anti-money laundering (AML) or know-your-customer (KYC) policies. Non-compliance may lead to legal issues for exchanges but leaves users vulnerable if funds are mishandled or if fraudulent activities occur without adequate oversight.
Financial Security Concerns
Since CEXs typically hold large sums of user funds in custodial wallets—sometimes covering millions of dollars—they become attractive targets for hackers seeking quick gains through theft. If an exchange suffers a security breach without sufficient insurance coverage or safeguards like cold storage solutions—a method where assets are kept offline—the impact on consumers can be devastating.
Moreover, many platforms lack comprehensive insurance policies protecting user deposits against loss from hacks or operational failures—a gap that heightens financial insecurity among traders relying heavily on these services.
Trading Safety Risks: Market Manipulation & Leverage
Centralized exchanges control critical aspects such as order books and trading volumes; this control makes them susceptible to market manipulation tactics like wash trading—which artificially inflates activity—and price manipulation schemes designed to deceive investors about market trends.
Additionally, high leverage offerings amplify both potential gains and losses—sometimes up to 100x—that can lead inexperienced traders into significant financial distress if markets move unfavorably quickly during volatile periods.
User Education & Transparency Deficits
Many consumers enter crypto markets without fully understanding associated risks due largely to limited transparency from some CEX providers regarding platform operations—including fee structures—and potential pitfalls involved in active trading strategies like margin calls or liquidation processes.
This knowledge gap increases the likelihood of uninformed decision-making leading users into risky trades they do not comprehend fully—highlighting the importance of educational initiatives by reputable platforms aiming at increasing awareness around safe practices within crypto ecosystems.
Recent Developments Impacting Consumer Protections
Regulatory Actions & Frameworks
Regulators worldwide are increasingly scrutinizing centralized cryptocurrency exchanges amid rising concerns over investor protection violations. For example:
- The U.S Securities and Exchange Commission (SEC) continues its legal battles with firms like Ripple Labs over whether certain tokens qualify as securities—a case that could influence how other tokens are regulated.
- The European Union’s proposed Markets in Crypto-Assets (MiCA) regulation aims at establishing comprehensive rules requiring greater transparency from CEX operators regarding operational standards—including disclosures about custody practices—and enforcing stricter compliance measures designed specifically for consumer safety.
These developments signal a shift toward more rigorous oversight intended at reducing fraud risk while enhancing overall trustworthiness within crypto markets.
Enhanced Security Protocol Implementations
Many leading centralized exchanges have responded proactively by investing heavily into advanced cybersecurity measures:
- Multi-signature wallets requiring multiple approvals before transactions proceed
- Cold storage solutions keeping most assets offline
- Regular third-party security audits aimed at identifying vulnerabilities early
Such steps aim not only at preventing breaches but also reassuring customers about platform safety standards.
Increased Focus on User Education & Transparency
Recognizing that well-informed traders make safer choices—and reduce platform liability—many top-tier CEXs now prioritize educational programs covering topics such as:
- Risk management strategies
- How custody works
- Recognizing scams
Furthermore, there’s an industry-wide push toward greater transparency concerning fee structures—including hidden charges—and detailed disclosures about operational policies related both directly linked risks involved during active trades.
Potential Fallout From Unaddressed Risks
Failure by centralized exchanges—or neglecting consumer protections—could result in serious consequences including:
- Loss of Trust: Repeated breaches erode confidence among existing users while deterring new entrants.
- Regulatory Crackdowns: Governments may impose harsher restrictions—or even shut down non-compliant platforms—to protect investors.
- Market Disruption: A significant exodus towards decentralized alternatives could destabilize traditional exchange models — impacting liquidity levels across global markets.
- Financial Losses: Users who fall victim due either hacking incidents or mismanagement face potentially devastating monetary setbacks without sufficient recourse options.
Moving Toward Safer Crypto Trading Environments
Addressing consumer protection challenges requires coordinated efforts across multiple fronts:
Regulators must establish clear guidelines tailored specifically toward digital asset custodianship.
Exchanges need ongoing investments into robust cybersecurity infrastructure coupled with transparent communication channels.
Users should prioritize education around safe trading practices—including verifying platform legitimacy before depositing funds—and stay updated on evolving regulations affecting their holdings.
By fostering an ecosystem rooted in trustworthiness through technological safeguards combined with regulatory clarity—not only will individual investors benefit—but broader market stability will be reinforced over time.
Protecting Yourself When Using Centralized Exchanges
While industry improvements continue apace—with enhanced security protocols becoming standard—it remains crucial for individual traders always practice good security hygiene:
- Use strong passwords unique per platform
- Enable two-factor authentication wherever possible
- Avoid sharing sensitive information publicly
- Keep abreast of official updates regarding your chosen exchange’s policies
Being proactive helps mitigate many common risks associated with centralized cryptocurrency platforms.
Final Thoughts
Centralized cryptocurrency exchanges serve vital functions within the digital asset ecosystem but come inherently bundled with various consumer protection challenges—from hacking vulnerabilities through regulatory uncertainties—all demanding ongoing attention from stakeholders including regulators, operators,and end-users alike.. As the industry matures—with increased emphasis on transparency,safety measures,and education—the hope is that these risks will diminish significantly over time — paving the way toward more secureand trustworthy crypto markets globally


kai
2025-05-09 15:14
What consumer-protection risks exist on centralized exchanges?
Consumer Protection Risks on Centralized Cryptocurrency Exchanges
Cryptocurrency trading has become increasingly mainstream, with centralized exchanges (CEXs) serving as the primary gateways for millions of users worldwide. While these platforms offer convenience, liquidity, and a wide range of services, they also pose significant consumer protection risks that users should be aware of. Understanding these risks is essential for anyone involved in crypto trading to make informed decisions and safeguard their assets.
What Are Centralized Cryptocurrency Exchanges?
Centralized exchanges are digital platforms that facilitate the buying, selling, and trading of cryptocurrencies by acting as intermediaries between traders. They manage order books, hold user funds in custodial wallets, and often provide additional features such as margin trading or staking options. Popular examples include Binance, Coinbase, Kraken, and Bitfinex.
Unlike decentralized exchanges (DEXs), which operate without a central authority and allow peer-to-peer transactions directly on blockchain networks, CEXs rely on their own infrastructure to execute trades. This centralization simplifies user experience but introduces specific risks related to security and regulatory oversight.
Key Consumer Protection Risks Associated with CEXs
Security Vulnerabilities
One of the most prominent concerns surrounding centralized exchanges is their vulnerability to cyberattacks. High-profile hacks have resulted in massive losses for users; notably, Mt. Gox's 2014 breach led to over 850,000 Bitcoins stolen—an amount worth billions today. These incidents expose how hackers target CEXs due to their large pools of assets stored centrally.
In addition to external threats like hacking attempts or data breaches exposing sensitive information such as personal details or account credentials—insider threats also pose a risk. Employees with access privileges might misuse their authority for personal gain or inadvertently compromise platform security if proper controls are not in place.
Regulatory Compliance Challenges
The regulatory landscape for cryptocurrencies remains complex and inconsistent across jurisdictions. Many countries lack clear frameworks governing CEX operations; some have outright bans while others impose stringent licensing requirements.
This ambiguity can leave consumers unprotected when disputes arise or when platforms fail to adhere strictly to financial regulations like anti-money laundering (AML) or know-your-customer (KYC) policies. Non-compliance may lead to legal issues for exchanges but leaves users vulnerable if funds are mishandled or if fraudulent activities occur without adequate oversight.
Financial Security Concerns
Since CEXs typically hold large sums of user funds in custodial wallets—sometimes covering millions of dollars—they become attractive targets for hackers seeking quick gains through theft. If an exchange suffers a security breach without sufficient insurance coverage or safeguards like cold storage solutions—a method where assets are kept offline—the impact on consumers can be devastating.
Moreover, many platforms lack comprehensive insurance policies protecting user deposits against loss from hacks or operational failures—a gap that heightens financial insecurity among traders relying heavily on these services.
Trading Safety Risks: Market Manipulation & Leverage
Centralized exchanges control critical aspects such as order books and trading volumes; this control makes them susceptible to market manipulation tactics like wash trading—which artificially inflates activity—and price manipulation schemes designed to deceive investors about market trends.
Additionally, high leverage offerings amplify both potential gains and losses—sometimes up to 100x—that can lead inexperienced traders into significant financial distress if markets move unfavorably quickly during volatile periods.
User Education & Transparency Deficits
Many consumers enter crypto markets without fully understanding associated risks due largely to limited transparency from some CEX providers regarding platform operations—including fee structures—and potential pitfalls involved in active trading strategies like margin calls or liquidation processes.
This knowledge gap increases the likelihood of uninformed decision-making leading users into risky trades they do not comprehend fully—highlighting the importance of educational initiatives by reputable platforms aiming at increasing awareness around safe practices within crypto ecosystems.
Recent Developments Impacting Consumer Protections
Regulatory Actions & Frameworks
Regulators worldwide are increasingly scrutinizing centralized cryptocurrency exchanges amid rising concerns over investor protection violations. For example:
- The U.S Securities and Exchange Commission (SEC) continues its legal battles with firms like Ripple Labs over whether certain tokens qualify as securities—a case that could influence how other tokens are regulated.
- The European Union’s proposed Markets in Crypto-Assets (MiCA) regulation aims at establishing comprehensive rules requiring greater transparency from CEX operators regarding operational standards—including disclosures about custody practices—and enforcing stricter compliance measures designed specifically for consumer safety.
These developments signal a shift toward more rigorous oversight intended at reducing fraud risk while enhancing overall trustworthiness within crypto markets.
Enhanced Security Protocol Implementations
Many leading centralized exchanges have responded proactively by investing heavily into advanced cybersecurity measures:
- Multi-signature wallets requiring multiple approvals before transactions proceed
- Cold storage solutions keeping most assets offline
- Regular third-party security audits aimed at identifying vulnerabilities early
Such steps aim not only at preventing breaches but also reassuring customers about platform safety standards.
Increased Focus on User Education & Transparency
Recognizing that well-informed traders make safer choices—and reduce platform liability—many top-tier CEXs now prioritize educational programs covering topics such as:
- Risk management strategies
- How custody works
- Recognizing scams
Furthermore, there’s an industry-wide push toward greater transparency concerning fee structures—including hidden charges—and detailed disclosures about operational policies related both directly linked risks involved during active trades.
Potential Fallout From Unaddressed Risks
Failure by centralized exchanges—or neglecting consumer protections—could result in serious consequences including:
- Loss of Trust: Repeated breaches erode confidence among existing users while deterring new entrants.
- Regulatory Crackdowns: Governments may impose harsher restrictions—or even shut down non-compliant platforms—to protect investors.
- Market Disruption: A significant exodus towards decentralized alternatives could destabilize traditional exchange models — impacting liquidity levels across global markets.
- Financial Losses: Users who fall victim due either hacking incidents or mismanagement face potentially devastating monetary setbacks without sufficient recourse options.
Moving Toward Safer Crypto Trading Environments
Addressing consumer protection challenges requires coordinated efforts across multiple fronts:
Regulators must establish clear guidelines tailored specifically toward digital asset custodianship.
Exchanges need ongoing investments into robust cybersecurity infrastructure coupled with transparent communication channels.
Users should prioritize education around safe trading practices—including verifying platform legitimacy before depositing funds—and stay updated on evolving regulations affecting their holdings.
By fostering an ecosystem rooted in trustworthiness through technological safeguards combined with regulatory clarity—not only will individual investors benefit—but broader market stability will be reinforced over time.
Protecting Yourself When Using Centralized Exchanges
While industry improvements continue apace—with enhanced security protocols becoming standard—it remains crucial for individual traders always practice good security hygiene:
- Use strong passwords unique per platform
- Enable two-factor authentication wherever possible
- Avoid sharing sensitive information publicly
- Keep abreast of official updates regarding your chosen exchange’s policies
Being proactive helps mitigate many common risks associated with centralized cryptocurrency platforms.
Final Thoughts
Centralized cryptocurrency exchanges serve vital functions within the digital asset ecosystem but come inherently bundled with various consumer protection challenges—from hacking vulnerabilities through regulatory uncertainties—all demanding ongoing attention from stakeholders including regulators, operators,and end-users alike.. As the industry matures—with increased emphasis on transparency,safety measures,and education—the hope is that these risks will diminish significantly over time — paving the way toward more secureand trustworthy crypto markets globally
Disclaimer:Contains third-party content. Not financial advice.
See Terms and Conditions.
